Compare commits
139 Commits
sysusers
...
2.3.182-20
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
fc649a565c | ||
|
|
113b38056b | ||
|
|
559276534d | ||
|
|
4acd9f8816 | ||
|
|
a7417a7242 | ||
|
|
d18ff69ec9 | ||
|
|
465a1a82d7 | ||
|
|
292f66138b | ||
|
|
0087768946 | ||
|
|
712340a027 | ||
|
|
1caac3f0b0 | ||
|
|
54a5dd6cbd | ||
|
|
6570177b0c | ||
|
|
f7ed992f24 | ||
|
|
4a18f8d18a | ||
|
|
b8884b6ac9 | ||
|
|
05e271af47 | ||
|
|
58e80a9db8 | ||
|
|
e16fc3605e | ||
|
|
2127ba90ee | ||
|
|
3373aef87d | ||
|
|
fa45e8ded7 | ||
|
|
6d0ead7b5b | ||
|
|
a2a6625f3b | ||
|
|
0d807d20f4 | ||
|
|
f4042263a3 | ||
|
|
a930f8233d | ||
|
|
7401008523 | ||
|
|
5199ea483e | ||
|
|
454a7a4799 | ||
|
|
6fb7733d8c | ||
|
|
ab17cbee31 | ||
|
|
9991f0cf95 | ||
|
|
44d46b06a2 | ||
|
|
ba7231f07d | ||
|
|
8dc11ea23a | ||
|
|
116a6a0acd | ||
|
|
311b69dc4a | ||
|
|
fd59acce5d | ||
|
|
956d3e4345 | ||
|
|
b8355b3a03 | ||
|
|
535b9f86db | ||
|
|
97c66a5404 | ||
|
|
6553beec99 | ||
|
|
e171dd52b8 | ||
|
|
27a837369d | ||
|
|
043b9f78e2 | ||
|
|
2f260a785f | ||
|
|
001b2dc6cc | ||
|
|
b13eedfbc2 | ||
|
|
dd70ef17b9 | ||
|
|
82dff3e9da | ||
|
|
d9cfd92b8f | ||
|
|
33cb771780 | ||
|
|
76cca8594d | ||
|
|
5c9c95ba1f | ||
|
|
e62bebeafe | ||
|
|
8a0e92cc6f | ||
|
|
3f9259dd0a | ||
|
|
30b9868de1 | ||
|
|
e88243c306 | ||
|
|
2128550df2 | ||
|
|
db67c0ed94 | ||
|
|
2e32c0d236 | ||
|
|
4b1ad1910d | ||
|
|
c337145b2c | ||
|
|
bd7b4c92bc | ||
|
|
33ebed3468 | ||
|
|
616bc40412 | ||
|
|
f00d9074ff | ||
|
|
9a692288e2 | ||
|
|
fea2b481e3 | ||
|
|
c17f0081ef | ||
|
|
fbf0803906 | ||
|
|
5deda45b66 | ||
|
|
3b8d8163b3 | ||
|
|
2dfd41bd3c | ||
|
|
49eead1d55 | ||
|
|
54cb3c3a5a | ||
|
|
9f2b920454 | ||
|
|
604af45661 | ||
|
|
3f435c5c1a | ||
|
|
7769af4541 | ||
|
|
9903be8120 | ||
|
|
991a601a3d | ||
|
|
86519d43dc | ||
|
|
179f669acf | ||
|
|
a02f878dcc | ||
|
|
32c29b28eb | ||
|
|
7bf2603414 | ||
|
|
4003876465 | ||
|
|
4c677961c4 | ||
|
|
e950d865d8 | ||
|
|
fd7a118664 | ||
|
|
d7906945df | ||
|
|
cb384ae024 | ||
|
|
7caead2387 | ||
|
|
4827c9e0d4 | ||
|
|
3b62fc63c9 | ||
|
|
ad32c2b1a5 | ||
|
|
f02f431dab | ||
|
|
812964e4d8 | ||
|
|
99805cc326 | ||
|
|
8d2b3f3dfe | ||
|
|
15f7fd8920 | ||
|
|
50460bf91e | ||
|
|
ee654f767a | ||
|
|
8c694a7ca3 | ||
|
|
9ac640fa67 | ||
|
|
db8d9fff2c | ||
|
|
811063268f | ||
|
|
f2b10a5a86 | ||
|
|
c69cac0e5f | ||
|
|
fed4433088 | ||
|
|
839cfcaefa | ||
|
|
3123407ef0 | ||
|
|
d24125c9e6 | ||
|
|
64dc278c95 | ||
|
|
626a824cd6 | ||
|
|
10ba3b4b5a | ||
|
|
1d059fc96e | ||
|
|
4c1585f8d8 | ||
|
|
e235957c00 | ||
|
|
2cc665bac6 | ||
|
|
d6e118dcd3 | ||
|
|
1d2534b2a1 | ||
|
|
484aa7b207 | ||
|
|
6986448239 | ||
|
|
f1d74dcd67 | ||
|
|
dd48d66c1c | ||
|
|
440f4e75c1 | ||
|
|
c795a70e9c | ||
|
|
340dbe8547 | ||
|
|
52a5e743e9 | ||
|
|
5ceff52796 | ||
|
|
f3a0ab0b2d | ||
|
|
4a7c994b66 | ||
|
|
07b8785f3d | ||
|
|
9a1092ab01 |
2
.github/.gitleaks.toml
vendored
@@ -536,7 +536,7 @@ secretGroup = 4
|
|||||||
|
|
||||||
[allowlist]
|
[allowlist]
|
||||||
description = "global allow lists"
|
description = "global allow lists"
|
||||||
regexes = ['''219-09-9999''', '''078-05-1120''', '''(9[0-9]{2}|666)-\d{2}-\d{4}''', '''RPM-GPG-KEY.*''']
|
regexes = ['''219-09-9999''', '''078-05-1120''', '''(9[0-9]{2}|666)-\d{2}-\d{4}''']
|
||||||
paths = [
|
paths = [
|
||||||
'''gitleaks.toml''',
|
'''gitleaks.toml''',
|
||||||
'''(.*?)(jpg|gif|doc|pdf|bin|svg|socket)$''',
|
'''(.*?)(jpg|gif|doc|pdf|bin|svg|socket)$''',
|
||||||
|
|||||||
2
.github/workflows/contrib.yml
vendored
@@ -11,7 +11,7 @@ jobs:
|
|||||||
steps:
|
steps:
|
||||||
- name: "Contributor Check"
|
- name: "Contributor Check"
|
||||||
if: (github.event.comment.body == 'recheck' || github.event.comment.body == 'I have read the CLA Document and I hereby sign the CLA') || github.event_name == 'pull_request_target'
|
if: (github.event.comment.body == 'recheck' || github.event.comment.body == 'I have read the CLA Document and I hereby sign the CLA') || github.event_name == 'pull_request_target'
|
||||||
uses: cla-assistant/github-action@v2.3.1
|
uses: cla-assistant/github-action@v2.1.3-beta
|
||||||
env:
|
env:
|
||||||
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
||||||
PERSONAL_ACCESS_TOKEN : ${{ secrets.PERSONAL_ACCESS_TOKEN }}
|
PERSONAL_ACCESS_TOKEN : ${{ secrets.PERSONAL_ACCESS_TOKEN }}
|
||||||
|
|||||||
14
.github/workflows/pythontest.yml
vendored
@@ -1,14 +1,6 @@
|
|||||||
name: python-test
|
name: python-test
|
||||||
|
|
||||||
on:
|
on: [push, pull_request]
|
||||||
push:
|
|
||||||
paths:
|
|
||||||
- "salt/sensoroni/files/analyzers/**"
|
|
||||||
- "salt/manager/tools/sbin"
|
|
||||||
pull_request:
|
|
||||||
paths:
|
|
||||||
- "salt/sensoroni/files/analyzers/**"
|
|
||||||
- "salt/manager/tools/sbin"
|
|
||||||
|
|
||||||
jobs:
|
jobs:
|
||||||
build:
|
build:
|
||||||
@@ -18,7 +10,7 @@ jobs:
|
|||||||
fail-fast: false
|
fail-fast: false
|
||||||
matrix:
|
matrix:
|
||||||
python-version: ["3.10"]
|
python-version: ["3.10"]
|
||||||
python-code-path: ["salt/sensoroni/files/analyzers", "salt/manager/tools/sbin"]
|
python-code-path: ["salt/sensoroni/files/analyzers"]
|
||||||
|
|
||||||
steps:
|
steps:
|
||||||
- uses: actions/checkout@v3
|
- uses: actions/checkout@v3
|
||||||
@@ -36,4 +28,4 @@ jobs:
|
|||||||
flake8 ${{ matrix.python-code-path }} --show-source --max-complexity=12 --doctests --max-line-length=200 --statistics
|
flake8 ${{ matrix.python-code-path }} --show-source --max-complexity=12 --doctests --max-line-length=200 --statistics
|
||||||
- name: Test with pytest
|
- name: Test with pytest
|
||||||
run: |
|
run: |
|
||||||
pytest ${{ matrix.python-code-path }} --cov=${{ matrix.python-code-path }} --doctest-modules --cov-report=term --cov-fail-under=100 --cov-config=pytest.ini
|
pytest ${{ matrix.python-code-path }} --cov=${{ matrix.python-code-path }} --doctest-modules --cov-report=term --cov-fail-under=100 --cov-config=${{ matrix.python-code-path }}/pytest.ini
|
||||||
|
|||||||
32
README.md
@@ -1,47 +1,41 @@
|
|||||||
## Security Onion 2.4
|
## Security Onion 2.3.182
|
||||||
|
|
||||||
Security Onion 2.4 is here!
|
Security Onion 2.3.182 is here!
|
||||||
|
|
||||||
## Screenshots
|
## Screenshots
|
||||||
|
|
||||||
Alerts
|
Alerts
|
||||||
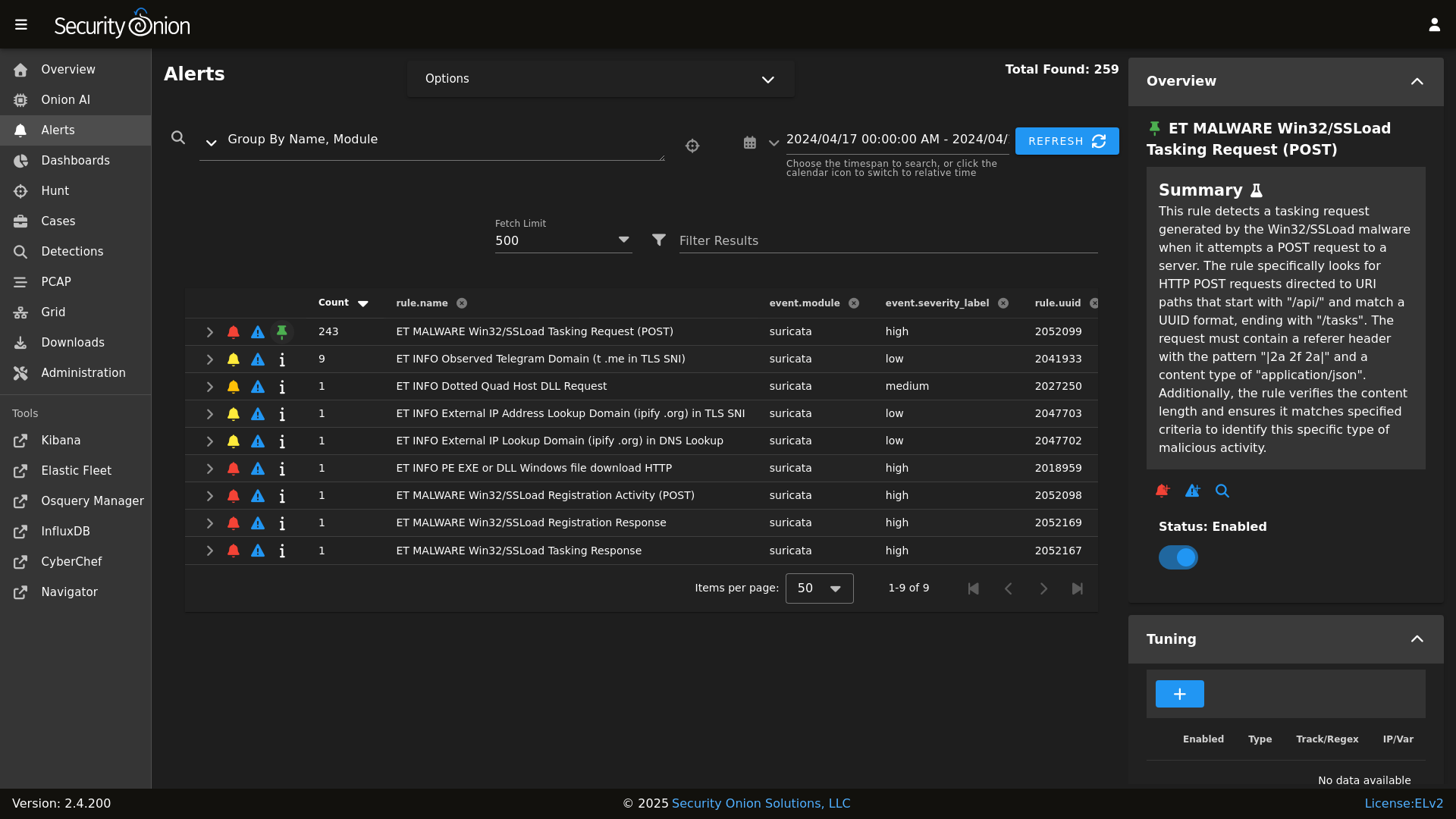
|

|
||||||
|
|
||||||
Dashboards
|
Dashboards
|
||||||

|

|
||||||
|
|
||||||
Hunt
|
Hunt
|
||||||

|

|
||||||
|
|
||||||
PCAP
|
Cases
|
||||||

|

|
||||||
|
|
||||||
Grid
|
|
||||||

|
|
||||||
|
|
||||||
Config
|
|
||||||

|
|
||||||
|
|
||||||
### Release Notes
|
### Release Notes
|
||||||
|
|
||||||
https://docs.securityonion.net/en/2.4/release-notes.html
|
https://docs.securityonion.net/en/2.3/release-notes.html
|
||||||
|
|
||||||
### Requirements
|
### Requirements
|
||||||
|
|
||||||
https://docs.securityonion.net/en/2.4/hardware.html
|
https://docs.securityonion.net/en/2.3/hardware.html
|
||||||
|
|
||||||
### Download
|
### Download
|
||||||
|
|
||||||
https://docs.securityonion.net/en/2.4/download.html
|
https://docs.securityonion.net/en/2.3/download.html
|
||||||
|
|
||||||
### Installation
|
### Installation
|
||||||
|
|
||||||
https://docs.securityonion.net/en/2.4/installation.html
|
https://docs.securityonion.net/en/2.3/installation.html
|
||||||
|
|
||||||
### FAQ
|
### FAQ
|
||||||
|
|
||||||
https://docs.securityonion.net/en/2.4/faq.html
|
https://docs.securityonion.net/en/2.3/faq.html
|
||||||
|
|
||||||
### Feedback
|
### Feedback
|
||||||
|
|
||||||
https://docs.securityonion.net/en/2.4/community-support.html
|
https://docs.securityonion.net/en/2.3/community-support.html
|
||||||
|
|||||||
@@ -4,8 +4,7 @@
|
|||||||
|
|
||||||
| Version | Supported |
|
| Version | Supported |
|
||||||
| ------- | ------------------ |
|
| ------- | ------------------ |
|
||||||
| 2.4.x | :white_check_mark: |
|
| 2.x.x | :white_check_mark: |
|
||||||
| 2.3.x | :white_check_mark: |
|
|
||||||
| 16.04.x | :x: |
|
| 16.04.x | :x: |
|
||||||
|
|
||||||
Security Onion 16.04 has reached End Of Life and is no longer supported.
|
Security Onion 16.04 has reached End Of Life and is no longer supported.
|
||||||
|
|||||||
@@ -1,46 +1,47 @@
|
|||||||
### 2.4.30-20231228 ISO image released on 2024/01/02
|
### 2.3.182-20221109 ISO image built on 2022/11/09
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
### Download and Verify
|
### Download and Verify
|
||||||
|
|
||||||
2.4.30-20231228 ISO image:
|
2.3.182-20221109 ISO image:
|
||||||
https://download.securityonion.net/file/securityonion/securityonion-2.4.30-20231228.iso
|
https://download.securityonion.net/file/securityonion/securityonion-2.3.182-20221109.iso
|
||||||
|
|
||||||
MD5: DBD47645CD6FA8358C51D8753046FB54
|
MD5: E472D5A7C64662435F84FD56491D8967
|
||||||
SHA1: 2494091065434ACB028F71444A5D16E8F8A11EDF
|
SHA1: D2069317553AF0A1FB4FB6FE15583FF4E8CB2973
|
||||||
SHA256: 3345AE1DC58AC7F29D82E60D9A36CDF8DE19B7DFF999D8C4F89C7BD36AEE7F1D
|
SHA256: A074EB38B88C0A00BDFD7FB75B4ECB7C46CB0B4CC993CAB81EFDC708B0075D2C
|
||||||
|
|
||||||
Signature for ISO image:
|
Signature for ISO image:
|
||||||
https://github.com/Security-Onion-Solutions/securityonion/raw/2.4/main/sigs/securityonion-2.4.30-20231228.iso.sig
|
https://github.com/Security-Onion-Solutions/securityonion/raw/master/sigs/securityonion-2.3.182-20221109.iso.sig
|
||||||
|
|
||||||
Signing key:
|
Signing key:
|
||||||
https://raw.githubusercontent.com/Security-Onion-Solutions/securityonion/2.4/main/KEYS
|
https://raw.githubusercontent.com/Security-Onion-Solutions/securityonion/master/KEYS
|
||||||
|
|
||||||
For example, here are the steps you can use on most Linux distributions to download and verify our Security Onion ISO image.
|
For example, here are the steps you can use on most Linux distributions to download and verify our Security Onion ISO image.
|
||||||
|
|
||||||
Download and import the signing key:
|
Download and import the signing key:
|
||||||
```
|
```
|
||||||
wget https://raw.githubusercontent.com/Security-Onion-Solutions/securityonion/2.4/main/KEYS -O - | gpg --import -
|
wget https://raw.githubusercontent.com/Security-Onion-Solutions/securityonion/master/KEYS -O - | gpg --import -
|
||||||
```
|
```
|
||||||
|
|
||||||
Download the signature file for the ISO:
|
Download the signature file for the ISO:
|
||||||
```
|
```
|
||||||
wget https://github.com/Security-Onion-Solutions/securityonion/raw/2.4/main/sigs/securityonion-2.4.30-20231228.iso.sig
|
wget https://github.com/Security-Onion-Solutions/securityonion/raw/master/sigs/securityonion-2.3.182-20221109.iso.sig
|
||||||
```
|
```
|
||||||
|
|
||||||
Download the ISO image:
|
Download the ISO image:
|
||||||
```
|
```
|
||||||
wget https://download.securityonion.net/file/securityonion/securityonion-2.4.30-20231228.iso
|
wget https://download.securityonion.net/file/securityonion/securityonion-2.3.182-20221109.iso
|
||||||
```
|
```
|
||||||
|
|
||||||
Verify the downloaded ISO image using the signature file:
|
Verify the downloaded ISO image using the signature file:
|
||||||
```
|
```
|
||||||
gpg --verify securityonion-2.4.30-20231228.iso.sig securityonion-2.4.30-20231228.iso
|
gpg --verify securityonion-2.3.182-20221109.iso.sig securityonion-2.3.182-20221109.iso
|
||||||
```
|
```
|
||||||
|
|
||||||
The output should show "Good signature" and the Primary key fingerprint should match what's shown below:
|
The output should show "Good signature" and the Primary key fingerprint should match what's shown below:
|
||||||
```
|
```
|
||||||
gpg: Signature made Thu 28 Dec 2023 10:08:31 AM EST using RSA key ID FE507013
|
gpg: Signature made Wed 09 Nov 2022 07:30:32 AM EST using RSA key ID FE507013
|
||||||
gpg: Good signature from "Security Onion Solutions, LLC <info@securityonionsolutions.com>"
|
gpg: Good signature from "Security Onion Solutions, LLC <info@securityonionsolutions.com>"
|
||||||
gpg: WARNING: This key is not certified with a trusted signature!
|
gpg: WARNING: This key is not certified with a trusted signature!
|
||||||
gpg: There is no indication that the signature belongs to the owner.
|
gpg: There is no indication that the signature belongs to the owner.
|
||||||
@@ -48,4 +49,4 @@ Primary key fingerprint: C804 A93D 36BE 0C73 3EA1 9644 7C10 60B7 FE50 7013
|
|||||||
```
|
```
|
||||||
|
|
||||||
Once you've verified the ISO image, you're ready to proceed to our Installation guide:
|
Once you've verified the ISO image, you're ready to proceed to our Installation guide:
|
||||||
https://docs.securityonion.net/en/2.4/installation.html
|
https://docs.securityonion.net/en/2.3/installation.html
|
||||||
|
Before Width: | Height: | Size: 21 KiB |
|
Before Width: | Height: | Size: 22 KiB |
|
Before Width: | Height: | Size: 12 KiB |
@@ -1,8 +1,8 @@
|
|||||||
{% import_yaml 'firewall/ports/ports.yaml' as default_portgroups %}
|
{% import_yaml 'firewall/portgroups.yaml' as default_portgroups %}
|
||||||
{% set default_portgroups = default_portgroups.firewall.ports %}
|
{% set default_portgroups = default_portgroups.firewall.aliases.ports %}
|
||||||
{% import_yaml 'firewall/ports/ports.local.yaml' as local_portgroups %}
|
{% import_yaml 'firewall/portgroups.local.yaml' as local_portgroups %}
|
||||||
{% if local_portgroups.firewall.ports %}
|
{% if local_portgroups.firewall.aliases.ports %}
|
||||||
{% set local_portgroups = local_portgroups.firewall.ports %}
|
{% set local_portgroups = local_portgroups.firewall.aliases.ports %}
|
||||||
{% else %}
|
{% else %}
|
||||||
{% set local_portgroups = {} %}
|
{% set local_portgroups = {} %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
@@ -12,6 +12,7 @@ role:
|
|||||||
eval:
|
eval:
|
||||||
fleet:
|
fleet:
|
||||||
heavynode:
|
heavynode:
|
||||||
|
helixsensor:
|
||||||
idh:
|
idh:
|
||||||
import:
|
import:
|
||||||
manager:
|
manager:
|
||||||
|
|||||||
82
files/firewall/hostgroups.local.yaml
Normal file
@@ -0,0 +1,82 @@
|
|||||||
|
firewall:
|
||||||
|
hostgroups:
|
||||||
|
analyst:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
beats_endpoint:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
beats_endpoint_ssl:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
elasticsearch_rest:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
endgame:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
fleet:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
heavy_node:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
idh:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
manager:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
minion:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
node:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
osquery_endpoint:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
receiver:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
search_node:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
sensor:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
strelka_frontend:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
syslog:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
wazuh_agent:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
wazuh_api:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
|
wazuh_authd:
|
||||||
|
ips:
|
||||||
|
delete:
|
||||||
|
insert:
|
||||||
3
files/firewall/portgroups.local.yaml
Normal file
@@ -0,0 +1,3 @@
|
|||||||
|
firewall:
|
||||||
|
aliases:
|
||||||
|
ports:
|
||||||
@@ -1,2 +0,0 @@
|
|||||||
firewall:
|
|
||||||
ports:
|
|
||||||
@@ -64,4 +64,10 @@ peer:
|
|||||||
.*:
|
.*:
|
||||||
- x509.sign_remote_certificate
|
- x509.sign_remote_certificate
|
||||||
|
|
||||||
|
reactor:
|
||||||
|
- 'so/fleet':
|
||||||
|
- salt://reactor/fleet.sls
|
||||||
|
- 'salt/beacon/*/watch_sqlite_db//opt/so/conf/kratos/db/sqlite.db':
|
||||||
|
- salt://reactor/kratos.sls
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@@ -45,10 +45,12 @@ echo " rootfs: $ROOTFS" >> $local_salt_dir/pillar/data/$TYPE.sls
|
|||||||
echo " nsmfs: $NSM" >> $local_salt_dir/pillar/data/$TYPE.sls
|
echo " nsmfs: $NSM" >> $local_salt_dir/pillar/data/$TYPE.sls
|
||||||
if [ $TYPE == 'sensorstab' ]; then
|
if [ $TYPE == 'sensorstab' ]; then
|
||||||
echo " monint: bond0" >> $local_salt_dir/pillar/data/$TYPE.sls
|
echo " monint: bond0" >> $local_salt_dir/pillar/data/$TYPE.sls
|
||||||
|
salt-call state.apply grafana queue=True
|
||||||
fi
|
fi
|
||||||
if [ $TYPE == 'evaltab' ] || [ $TYPE == 'standalonetab' ]; then
|
if [ $TYPE == 'evaltab' ] || [ $TYPE == 'standalonetab' ]; then
|
||||||
echo " monint: bond0" >> $local_salt_dir/pillar/data/$TYPE.sls
|
echo " monint: bond0" >> $local_salt_dir/pillar/data/$TYPE.sls
|
||||||
if [ ! $10 ]; then
|
if [ ! $10 ]; then
|
||||||
|
salt-call state.apply grafana queue=True
|
||||||
salt-call state.apply utility queue=True
|
salt-call state.apply utility queue=True
|
||||||
fi
|
fi
|
||||||
fi
|
fi
|
||||||
|
|||||||
13
pillar/logrotate/init.sls
Normal file
@@ -0,0 +1,13 @@
|
|||||||
|
logrotate:
|
||||||
|
conf: |
|
||||||
|
daily
|
||||||
|
rotate 14
|
||||||
|
missingok
|
||||||
|
copytruncate
|
||||||
|
compress
|
||||||
|
create
|
||||||
|
extension .log
|
||||||
|
dateext
|
||||||
|
dateyesterday
|
||||||
|
group_conf: |
|
||||||
|
su root socore
|
||||||
42
pillar/logstash/helix.sls
Normal file
@@ -0,0 +1,42 @@
|
|||||||
|
logstash:
|
||||||
|
pipelines:
|
||||||
|
helix:
|
||||||
|
config:
|
||||||
|
- so/0010_input_hhbeats.conf
|
||||||
|
- so/1033_preprocess_snort.conf
|
||||||
|
- so/1100_preprocess_bro_conn.conf
|
||||||
|
- so/1101_preprocess_bro_dhcp.conf
|
||||||
|
- so/1102_preprocess_bro_dns.conf
|
||||||
|
- so/1103_preprocess_bro_dpd.conf
|
||||||
|
- so/1104_preprocess_bro_files.conf
|
||||||
|
- so/1105_preprocess_bro_ftp.conf
|
||||||
|
- so/1106_preprocess_bro_http.conf
|
||||||
|
- so/1107_preprocess_bro_irc.conf
|
||||||
|
- so/1108_preprocess_bro_kerberos.conf
|
||||||
|
- so/1109_preprocess_bro_notice.conf
|
||||||
|
- so/1110_preprocess_bro_rdp.conf
|
||||||
|
- so/1111_preprocess_bro_signatures.conf
|
||||||
|
- so/1112_preprocess_bro_smtp.conf
|
||||||
|
- so/1113_preprocess_bro_snmp.conf
|
||||||
|
- so/1114_preprocess_bro_software.conf
|
||||||
|
- so/1115_preprocess_bro_ssh.conf
|
||||||
|
- so/1116_preprocess_bro_ssl.conf
|
||||||
|
- so/1117_preprocess_bro_syslog.conf
|
||||||
|
- so/1118_preprocess_bro_tunnel.conf
|
||||||
|
- so/1119_preprocess_bro_weird.conf
|
||||||
|
- so/1121_preprocess_bro_mysql.conf
|
||||||
|
- so/1122_preprocess_bro_socks.conf
|
||||||
|
- so/1123_preprocess_bro_x509.conf
|
||||||
|
- so/1124_preprocess_bro_intel.conf
|
||||||
|
- so/1125_preprocess_bro_modbus.conf
|
||||||
|
- so/1126_preprocess_bro_sip.conf
|
||||||
|
- so/1127_preprocess_bro_radius.conf
|
||||||
|
- so/1128_preprocess_bro_pe.conf
|
||||||
|
- so/1129_preprocess_bro_rfb.conf
|
||||||
|
- so/1130_preprocess_bro_dnp3.conf
|
||||||
|
- so/1131_preprocess_bro_smb_files.conf
|
||||||
|
- so/1132_preprocess_bro_smb_mapping.conf
|
||||||
|
- so/1133_preprocess_bro_ntlm.conf
|
||||||
|
- so/1134_preprocess_bro_dce_rpc.conf
|
||||||
|
- so/8001_postprocess_common_ip_augmentation.conf
|
||||||
|
- so/9997_output_helix.conf.jinja
|
||||||
@@ -3,8 +3,6 @@ logstash:
|
|||||||
port_bindings:
|
port_bindings:
|
||||||
- 0.0.0.0:3765:3765
|
- 0.0.0.0:3765:3765
|
||||||
- 0.0.0.0:5044:5044
|
- 0.0.0.0:5044:5044
|
||||||
- 0.0.0.0:5055:5055
|
|
||||||
- 0.0.0.0:5056:5056
|
|
||||||
- 0.0.0.0:5644:5644
|
- 0.0.0.0:5644:5644
|
||||||
- 0.0.0.0:6050:6050
|
- 0.0.0.0:6050:6050
|
||||||
- 0.0.0.0:6051:6051
|
- 0.0.0.0:6051:6051
|
||||||
|
|||||||
9
pillar/logstash/manager.sls
Normal file
@@ -0,0 +1,9 @@
|
|||||||
|
logstash:
|
||||||
|
pipelines:
|
||||||
|
manager:
|
||||||
|
config:
|
||||||
|
- so/0009_input_beats.conf
|
||||||
|
- so/0010_input_hhbeats.conf
|
||||||
|
- so/0011_input_endgame.conf
|
||||||
|
- so/9999_output_redis.conf.jinja
|
||||||
|
|
||||||
@@ -2,28 +2,24 @@
|
|||||||
{% set cached_grains = salt.saltutil.runner('cache.grains', tgt='*') %}
|
{% set cached_grains = salt.saltutil.runner('cache.grains', tgt='*') %}
|
||||||
{% for minionid, ip in salt.saltutil.runner(
|
{% for minionid, ip in salt.saltutil.runner(
|
||||||
'mine.get',
|
'mine.get',
|
||||||
tgt='G@role:so-manager or G@role:so-managersearch or G@role:so-standalone or G@role:so-searchnode or G@role:so-heavynode or G@role:so-receiver or G@role:so-fleet ',
|
tgt='G@role:so-manager or G@role:so-managersearch or G@role:so-standalone or G@role:so-node or G@role:so-heavynode or G@role:so-receiver or G@role:so-helix',
|
||||||
fun='network.ip_addrs',
|
fun='network.ip_addrs',
|
||||||
tgt_type='compound') | dictsort()
|
tgt_type='compound') | dictsort()
|
||||||
%}
|
%}
|
||||||
|
|
||||||
# only add a node to the pillar if it returned an ip from the mine
|
{% set hostname = cached_grains[minionid]['host'] %}
|
||||||
{% if ip | length > 0%}
|
{% set node_type = minionid.split('_')[1] %}
|
||||||
{% set hostname = cached_grains[minionid]['host'] %}
|
{% if node_type not in node_types.keys() %}
|
||||||
{% set node_type = minionid.split('_')[1] %}
|
{% do node_types.update({node_type: {hostname: ip[0]}}) %}
|
||||||
{% if node_type not in node_types.keys() %}
|
{% else %}
|
||||||
{% do node_types.update({node_type: {hostname: ip[0]}}) %}
|
{% if hostname not in node_types[node_type] %}
|
||||||
|
{% do node_types[node_type].update({hostname: ip[0]}) %}
|
||||||
{% else %}
|
{% else %}
|
||||||
{% if hostname not in node_types[node_type] %}
|
{% do node_types[node_type][hostname].update(ip[0]) %}
|
||||||
{% do node_types[node_type].update({hostname: ip[0]}) %}
|
|
||||||
{% else %}
|
|
||||||
{% do node_types[node_type][hostname].update(ip[0]) %}
|
|
||||||
{% endif %}
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% endfor %}
|
{% endfor %}
|
||||||
|
|
||||||
|
|
||||||
logstash:
|
logstash:
|
||||||
nodes:
|
nodes:
|
||||||
{% for node_type, values in node_types.items() %}
|
{% for node_type, values in node_types.items() %}
|
||||||
|
|||||||
9
pillar/logstash/receiver.sls
Normal file
@@ -0,0 +1,9 @@
|
|||||||
|
logstash:
|
||||||
|
pipelines:
|
||||||
|
receiver:
|
||||||
|
config:
|
||||||
|
- so/0009_input_beats.conf
|
||||||
|
- so/0010_input_hhbeats.conf
|
||||||
|
- so/0011_input_endgame.conf
|
||||||
|
- so/9999_output_redis.conf.jinja
|
||||||
|
|
||||||
18
pillar/logstash/search.sls
Normal file
@@ -0,0 +1,18 @@
|
|||||||
|
logstash:
|
||||||
|
pipelines:
|
||||||
|
search:
|
||||||
|
config:
|
||||||
|
- so/0900_input_redis.conf.jinja
|
||||||
|
- so/9000_output_zeek.conf.jinja
|
||||||
|
- so/9002_output_import.conf.jinja
|
||||||
|
- so/9034_output_syslog.conf.jinja
|
||||||
|
- so/9050_output_filebeatmodules.conf.jinja
|
||||||
|
- so/9100_output_osquery.conf.jinja
|
||||||
|
- so/9400_output_suricata.conf.jinja
|
||||||
|
- so/9500_output_beats.conf.jinja
|
||||||
|
- so/9600_output_ossec.conf.jinja
|
||||||
|
- so/9700_output_strelka.conf.jinja
|
||||||
|
- so/9800_output_logscan.conf.jinja
|
||||||
|
- so/9801_output_rita.conf.jinja
|
||||||
|
- so/9802_output_kratos.conf.jinja
|
||||||
|
- so/9900_output_endgame.conf.jinja
|
||||||
@@ -1,35 +1,33 @@
|
|||||||
{% set node_types = {} %}
|
{% set node_types = {} %}
|
||||||
{% set manage_alived = salt.saltutil.runner('manage.alived', show_ip=True) %}
|
{% set manage_alived = salt.saltutil.runner('manage.alived', show_ip=True) %}
|
||||||
|
{% set manager = grains.master %}
|
||||||
|
{% set manager_type = manager.split('_')|last %}
|
||||||
{% for minionid, ip in salt.saltutil.runner('mine.get', tgt='*', fun='network.ip_addrs', tgt_type='glob') | dictsort() %}
|
{% for minionid, ip in salt.saltutil.runner('mine.get', tgt='*', fun='network.ip_addrs', tgt_type='glob') | dictsort() %}
|
||||||
{% set hostname = minionid.split('_')[0] %}
|
{% set hostname = minionid.split('_')[0] %}
|
||||||
{% set node_type = minionid.split('_')[1] %}
|
{% set node_type = minionid.split('_')[1] %}
|
||||||
{% set is_alive = False %}
|
{% set is_alive = False %}
|
||||||
|
{% if minionid in manage_alived.keys() %}
|
||||||
# only add a node to the pillar if it returned an ip from the mine
|
{% if ip[0] == manage_alived[minionid] %}
|
||||||
{% if ip | length > 0%}
|
{% set is_alive = True %}
|
||||||
{% if minionid in manage_alived.keys() %}
|
|
||||||
{% if ip[0] == manage_alived[minionid] %}
|
|
||||||
{% set is_alive = True %}
|
|
||||||
{% endif %}
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% if node_type not in node_types.keys() %}
|
{% endif %}
|
||||||
{% do node_types.update({node_type: {hostname: {'ip':ip[0], 'alive':is_alive }}}) %}
|
{% if node_type not in node_types.keys() %}
|
||||||
|
{% do node_types.update({node_type: {hostname: {'ip':ip[0], 'alive':is_alive }}}) %}
|
||||||
|
{% else %}
|
||||||
|
{% if hostname not in node_types[node_type] %}
|
||||||
|
{% do node_types[node_type].update({hostname: {'ip':ip[0], 'alive':is_alive}}) %}
|
||||||
{% else %}
|
{% else %}
|
||||||
{% if hostname not in node_types[node_type] %}
|
{% do node_types[node_type][hostname].update({'ip':ip[0], 'alive':is_alive}) %}
|
||||||
{% do node_types[node_type].update({hostname: {'ip':ip[0], 'alive':is_alive}}) %}
|
|
||||||
{% else %}
|
|
||||||
{% do node_types[node_type][hostname].update({'ip':ip[0], 'alive':is_alive}) %}
|
|
||||||
{% endif %}
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% endfor %}
|
{% endfor %}
|
||||||
|
|
||||||
node_data:
|
node_data:
|
||||||
{% for node_type, host_values in node_types.items() %}
|
{% for node_type, host_values in node_types.items() %}
|
||||||
|
{{node_type}}:
|
||||||
{% for hostname, details in host_values.items() %}
|
{% for hostname, details in host_values.items() %}
|
||||||
{{hostname}}:
|
{{hostname}}:
|
||||||
ip: {{details.ip}}
|
ip: {{details.ip}}
|
||||||
alive: {{ details.alive }}
|
alive: {{ details.alive }}
|
||||||
role: {{node_type}}
|
|
||||||
{% endfor %}
|
{% endfor %}
|
||||||
{% endfor %}
|
{% endfor %}
|
||||||
|
|||||||
@@ -1,14 +0,0 @@
|
|||||||
# Copyright Jason Ertel (github.com/jertel).
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with
|
|
||||||
# the Elastic License 2.0.
|
|
||||||
|
|
||||||
# Note: Per the Elastic License 2.0, the second limitation states:
|
|
||||||
#
|
|
||||||
# "You may not move, change, disable, or circumvent the license key functionality
|
|
||||||
# in the software, and you may not remove or obscure any functionality in the
|
|
||||||
# software that is protected by the license key."
|
|
||||||
|
|
||||||
# This file is generated by Security Onion and contains a list of license-enabled features.
|
|
||||||
features: []
|
|
||||||
44
pillar/thresholding/pillar.example
Normal file
@@ -0,0 +1,44 @@
|
|||||||
|
thresholding:
|
||||||
|
sids:
|
||||||
|
8675309:
|
||||||
|
- threshold:
|
||||||
|
gen_id: 1
|
||||||
|
type: threshold
|
||||||
|
track: by_src
|
||||||
|
count: 10
|
||||||
|
seconds: 10
|
||||||
|
- threshold:
|
||||||
|
gen_id: 1
|
||||||
|
type: limit
|
||||||
|
track: by_dst
|
||||||
|
count: 100
|
||||||
|
seconds: 30
|
||||||
|
- rate_filter:
|
||||||
|
gen_id: 1
|
||||||
|
track: by_rule
|
||||||
|
count: 50
|
||||||
|
seconds: 30
|
||||||
|
new_action: alert
|
||||||
|
timeout: 30
|
||||||
|
- suppress:
|
||||||
|
gen_id: 1
|
||||||
|
track: by_either
|
||||||
|
ip: 10.10.3.7
|
||||||
|
11223344:
|
||||||
|
- threshold:
|
||||||
|
gen_id: 1
|
||||||
|
type: limit
|
||||||
|
track: by_dst
|
||||||
|
count: 10
|
||||||
|
seconds: 10
|
||||||
|
- rate_filter:
|
||||||
|
gen_id: 1
|
||||||
|
track: by_src
|
||||||
|
count: 50
|
||||||
|
seconds: 20
|
||||||
|
new_action: pass
|
||||||
|
timeout: 60
|
||||||
|
- suppress:
|
||||||
|
gen_id: 1
|
||||||
|
track: by_src
|
||||||
|
ip: 10.10.3.0/24
|
||||||
20
pillar/thresholding/pillar.usage
Normal file
@@ -0,0 +1,20 @@
|
|||||||
|
thresholding:
|
||||||
|
sids:
|
||||||
|
<signature id>:
|
||||||
|
- threshold:
|
||||||
|
gen_id: <generator id>
|
||||||
|
type: <threshold | limit | both>
|
||||||
|
track: <by_src | by_dst>
|
||||||
|
count: <count>
|
||||||
|
seconds: <seconds>
|
||||||
|
- rate_filter:
|
||||||
|
gen_id: <generator id>
|
||||||
|
track: <by_src | by_dst | by_rule | by_both>
|
||||||
|
count: <count>
|
||||||
|
seconds: <seconds>
|
||||||
|
new_action: <alert | pass>
|
||||||
|
timeout: <seconds>
|
||||||
|
- suppress:
|
||||||
|
gen_id: <generator id>
|
||||||
|
track: <by_src | by_dst | by_either>
|
||||||
|
ip: <ip | subnet>
|
||||||
350
pillar/top.sls
@@ -1,298 +1,136 @@
|
|||||||
base:
|
base:
|
||||||
'*':
|
'*':
|
||||||
- global.soc_global
|
|
||||||
- global.adv_global
|
|
||||||
- docker.soc_docker
|
|
||||||
- docker.adv_docker
|
|
||||||
- influxdb.token
|
|
||||||
- logrotate.soc_logrotate
|
|
||||||
- logrotate.adv_logrotate
|
|
||||||
- ntp.soc_ntp
|
|
||||||
- ntp.adv_ntp
|
|
||||||
- patch.needs_restarting
|
- patch.needs_restarting
|
||||||
- patch.soc_patch
|
- logrotate
|
||||||
- patch.adv_patch
|
|
||||||
- sensoroni.soc_sensoroni
|
|
||||||
- sensoroni.adv_sensoroni
|
|
||||||
- telegraf.soc_telegraf
|
|
||||||
- telegraf.adv_telegraf
|
|
||||||
- users
|
|
||||||
|
|
||||||
'* and not *_desktop':
|
'* and not *_eval and not *_import':
|
||||||
- firewall.soc_firewall
|
- logstash.nodes
|
||||||
- firewall.adv_firewall
|
|
||||||
- nginx.soc_nginx
|
'*_eval or *_helixsensor or *_heavynode or *_sensor or *_standalone or *_import':
|
||||||
- nginx.adv_nginx
|
- match: compound
|
||||||
- node_data.ips
|
- zeek
|
||||||
|
|
||||||
|
'*_managersearch or *_heavynode':
|
||||||
|
- match: compound
|
||||||
|
- logstash
|
||||||
|
- logstash.manager
|
||||||
|
- logstash.search
|
||||||
|
- elasticsearch.index_templates
|
||||||
|
|
||||||
|
'*_manager':
|
||||||
|
- logstash
|
||||||
|
- logstash.manager
|
||||||
|
- elasticsearch.index_templates
|
||||||
|
|
||||||
'*_manager or *_managersearch':
|
'*_manager or *_managersearch':
|
||||||
- match: compound
|
- match: compound
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
- data.*
|
||||||
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
||||||
- elasticsearch.auth
|
- elasticsearch.auth
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
||||||
- kibana.secrets
|
- kibana.secrets
|
||||||
{% endif %}
|
{% endif %}
|
||||||
- secrets
|
- secrets
|
||||||
- manager.soc_manager
|
- global
|
||||||
- manager.adv_manager
|
|
||||||
- idstools.soc_idstools
|
|
||||||
- idstools.adv_idstools
|
|
||||||
- logstash.nodes
|
|
||||||
- logstash.soc_logstash
|
|
||||||
- logstash.adv_logstash
|
|
||||||
- soc.soc_soc
|
|
||||||
- soc.adv_soc
|
|
||||||
- soc.license
|
|
||||||
- soctopus.soc_soctopus
|
|
||||||
- soctopus.adv_soctopus
|
|
||||||
- kibana.soc_kibana
|
|
||||||
- kibana.adv_kibana
|
|
||||||
- kratos.soc_kratos
|
|
||||||
- kratos.adv_kratos
|
|
||||||
- redis.soc_redis
|
|
||||||
- redis.adv_redis
|
|
||||||
- influxdb.soc_influxdb
|
|
||||||
- influxdb.adv_influxdb
|
|
||||||
- elasticsearch.soc_elasticsearch
|
|
||||||
- elasticsearch.adv_elasticsearch
|
|
||||||
- elasticfleet.soc_elasticfleet
|
|
||||||
- elasticfleet.adv_elasticfleet
|
|
||||||
- elastalert.soc_elastalert
|
|
||||||
- elastalert.adv_elastalert
|
|
||||||
- backup.soc_backup
|
|
||||||
- backup.adv_backup
|
|
||||||
- soctopus.soc_soctopus
|
|
||||||
- soctopus.adv_soctopus
|
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_sensor':
|
'*_sensor':
|
||||||
|
- zeeklogs
|
||||||
- healthcheck.sensor
|
- healthcheck.sensor
|
||||||
- strelka.soc_strelka
|
- global
|
||||||
- strelka.adv_strelka
|
|
||||||
- zeek.soc_zeek
|
|
||||||
- zeek.adv_zeek
|
|
||||||
- bpf.soc_bpf
|
|
||||||
- bpf.adv_bpf
|
|
||||||
- pcap.soc_pcap
|
|
||||||
- pcap.adv_pcap
|
|
||||||
- suricata.soc_suricata
|
|
||||||
- suricata.adv_suricata
|
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_eval':
|
'*_eval':
|
||||||
|
- data.*
|
||||||
|
- zeeklogs
|
||||||
- secrets
|
- secrets
|
||||||
- healthcheck.eval
|
- healthcheck.eval
|
||||||
- elasticsearch.index_templates
|
- elasticsearch.index_templates
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
||||||
- elasticsearch.auth
|
- elasticsearch.auth
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
||||||
- kibana.secrets
|
- kibana.secrets
|
||||||
{% endif %}
|
{% endif %}
|
||||||
- kratos.soc_kratos
|
- global
|
||||||
- elasticsearch.soc_elasticsearch
|
|
||||||
- elasticsearch.adv_elasticsearch
|
|
||||||
- elasticfleet.soc_elasticfleet
|
|
||||||
- elasticfleet.adv_elasticfleet
|
|
||||||
- elastalert.soc_elastalert
|
|
||||||
- elastalert.adv_elastalert
|
|
||||||
- manager.soc_manager
|
|
||||||
- manager.adv_manager
|
|
||||||
- idstools.soc_idstools
|
|
||||||
- idstools.adv_idstools
|
|
||||||
- soc.soc_soc
|
|
||||||
- soc.adv_soc
|
|
||||||
- soc.license
|
|
||||||
- soctopus.soc_soctopus
|
|
||||||
- soctopus.adv_soctopus
|
|
||||||
- kibana.soc_kibana
|
|
||||||
- kibana.adv_kibana
|
|
||||||
- strelka.soc_strelka
|
|
||||||
- strelka.adv_strelka
|
|
||||||
- kratos.soc_kratos
|
|
||||||
- kratos.adv_kratos
|
|
||||||
- redis.soc_redis
|
|
||||||
- redis.adv_redis
|
|
||||||
- influxdb.soc_influxdb
|
|
||||||
- influxdb.adv_influxdb
|
|
||||||
- backup.soc_backup
|
|
||||||
- backup.adv_backup
|
|
||||||
- zeek.soc_zeek
|
|
||||||
- zeek.adv_zeek
|
|
||||||
- bpf.soc_bpf
|
|
||||||
- bpf.adv_bpf
|
|
||||||
- pcap.soc_pcap
|
|
||||||
- pcap.adv_pcap
|
|
||||||
- suricata.soc_suricata
|
|
||||||
- suricata.adv_suricata
|
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_standalone':
|
'*_standalone':
|
||||||
- logstash.nodes
|
- logstash
|
||||||
- logstash.soc_logstash
|
- logstash.manager
|
||||||
- logstash.adv_logstash
|
- logstash.search
|
||||||
- elasticsearch.index_templates
|
- elasticsearch.index_templates
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
||||||
- elasticsearch.auth
|
- elasticsearch.auth
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
||||||
- kibana.secrets
|
- kibana.secrets
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
- data.*
|
||||||
|
- zeeklogs
|
||||||
- secrets
|
- secrets
|
||||||
- healthcheck.standalone
|
- healthcheck.standalone
|
||||||
- idstools.soc_idstools
|
- global
|
||||||
- idstools.adv_idstools
|
- minions.{{ grains.id }}
|
||||||
- kratos.soc_kratos
|
|
||||||
- kratos.adv_kratos
|
'*_node':
|
||||||
- redis.soc_redis
|
- global
|
||||||
- redis.adv_redis
|
|
||||||
- influxdb.soc_influxdb
|
|
||||||
- influxdb.adv_influxdb
|
|
||||||
- elasticsearch.soc_elasticsearch
|
|
||||||
- elasticsearch.adv_elasticsearch
|
|
||||||
- elasticfleet.soc_elasticfleet
|
|
||||||
- elasticfleet.adv_elasticfleet
|
|
||||||
- elastalert.soc_elastalert
|
|
||||||
- elastalert.adv_elastalert
|
|
||||||
- manager.soc_manager
|
|
||||||
- manager.adv_manager
|
|
||||||
- soc.soc_soc
|
|
||||||
- soc.adv_soc
|
|
||||||
- soc.license
|
|
||||||
- soctopus.soc_soctopus
|
|
||||||
- soctopus.adv_soctopus
|
|
||||||
- kibana.soc_kibana
|
|
||||||
- kibana.adv_kibana
|
|
||||||
- strelka.soc_strelka
|
|
||||||
- strelka.adv_strelka
|
|
||||||
- backup.soc_backup
|
|
||||||
- backup.adv_backup
|
|
||||||
- zeek.soc_zeek
|
|
||||||
- zeek.adv_zeek
|
|
||||||
- bpf.soc_bpf
|
|
||||||
- bpf.adv_bpf
|
|
||||||
- pcap.soc_pcap
|
|
||||||
- pcap.adv_pcap
|
|
||||||
- suricata.soc_suricata
|
|
||||||
- suricata.adv_suricata
|
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_heavynode':
|
'*_heavynode':
|
||||||
|
- zeeklogs
|
||||||
- elasticsearch.auth
|
- elasticsearch.auth
|
||||||
- logstash.nodes
|
- global
|
||||||
- logstash.soc_logstash
|
|
||||||
- logstash.adv_logstash
|
|
||||||
- elasticsearch.soc_elasticsearch
|
|
||||||
- elasticsearch.adv_elasticsearch
|
|
||||||
- redis.soc_redis
|
|
||||||
- redis.adv_redis
|
|
||||||
- zeek.soc_zeek
|
|
||||||
- zeek.adv_zeek
|
|
||||||
- bpf.soc_bpf
|
|
||||||
- bpf.adv_bpf
|
|
||||||
- pcap.soc_pcap
|
|
||||||
- pcap.adv_pcap
|
|
||||||
- suricata.soc_suricata
|
|
||||||
- suricata.adv_suricata
|
|
||||||
- strelka.soc_strelka
|
|
||||||
- strelka.adv_strelka
|
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_idh':
|
'*_helixsensor':
|
||||||
- idh.soc_idh
|
- fireeye
|
||||||
- idh.adv_idh
|
- zeeklogs
|
||||||
|
- logstash
|
||||||
|
- logstash.helix
|
||||||
|
- global
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_searchnode':
|
|
||||||
- logstash.nodes
|
|
||||||
- logstash.soc_logstash
|
|
||||||
- logstash.adv_logstash
|
|
||||||
- elasticsearch.soc_elasticsearch
|
|
||||||
- elasticsearch.adv_elasticsearch
|
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
|
||||||
- elasticsearch.auth
|
|
||||||
{% endif %}
|
|
||||||
- redis.soc_redis
|
|
||||||
- redis.adv_redis
|
|
||||||
- minions.{{ grains.id }}
|
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_receiver':
|
|
||||||
- logstash.nodes
|
|
||||||
- logstash.soc_logstash
|
|
||||||
- logstash.adv_logstash
|
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
|
||||||
- elasticsearch.auth
|
|
||||||
{% endif %}
|
|
||||||
- redis.soc_redis
|
|
||||||
- redis.adv_redis
|
|
||||||
- minions.{{ grains.id }}
|
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_import':
|
|
||||||
- secrets
|
|
||||||
- elasticsearch.index_templates
|
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
|
||||||
- elasticsearch.auth
|
|
||||||
{% endif %}
|
|
||||||
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
|
||||||
- kibana.secrets
|
|
||||||
{% endif %}
|
|
||||||
- kratos.soc_kratos
|
|
||||||
- elasticsearch.soc_elasticsearch
|
|
||||||
- elasticsearch.adv_elasticsearch
|
|
||||||
- elasticfleet.soc_elasticfleet
|
|
||||||
- elasticfleet.adv_elasticfleet
|
|
||||||
- elastalert.soc_elastalert
|
|
||||||
- elastalert.adv_elastalert
|
|
||||||
- manager.soc_manager
|
|
||||||
- manager.adv_manager
|
|
||||||
- soc.soc_soc
|
|
||||||
- soc.adv_soc
|
|
||||||
- soc.license
|
|
||||||
- soctopus.soc_soctopus
|
|
||||||
- soctopus.adv_soctopus
|
|
||||||
- kibana.soc_kibana
|
|
||||||
- kibana.adv_kibana
|
|
||||||
- backup.soc_backup
|
|
||||||
- backup.adv_backup
|
|
||||||
- kratos.soc_kratos
|
|
||||||
- kratos.adv_kratos
|
|
||||||
- redis.soc_redis
|
|
||||||
- redis.adv_redis
|
|
||||||
- influxdb.soc_influxdb
|
|
||||||
- influxdb.adv_influxdb
|
|
||||||
- zeek.soc_zeek
|
|
||||||
- zeek.adv_zeek
|
|
||||||
- bpf.soc_bpf
|
|
||||||
- bpf.adv_bpf
|
|
||||||
- pcap.soc_pcap
|
|
||||||
- pcap.adv_pcap
|
|
||||||
- suricata.soc_suricata
|
|
||||||
- suricata.adv_suricata
|
|
||||||
- strelka.soc_strelka
|
|
||||||
- strelka.adv_strelka
|
|
||||||
- minions.{{ grains.id }}
|
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_fleet':
|
'*_fleet':
|
||||||
- backup.soc_backup
|
- data.*
|
||||||
- backup.adv_backup
|
- secrets
|
||||||
- logstash.nodes
|
- global
|
||||||
- logstash.soc_logstash
|
|
||||||
- logstash.adv_logstash
|
|
||||||
- elasticfleet.soc_elasticfleet
|
|
||||||
- elasticfleet.adv_elasticfleet
|
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|
||||||
'*_desktop':
|
'*_idh':
|
||||||
|
- data.*
|
||||||
|
- global
|
||||||
|
- minions.{{ grains.id }}
|
||||||
|
|
||||||
|
'*_searchnode':
|
||||||
|
- logstash
|
||||||
|
- logstash.search
|
||||||
|
- elasticsearch.index_templates
|
||||||
|
- elasticsearch.auth
|
||||||
|
- global
|
||||||
|
- minions.{{ grains.id }}
|
||||||
|
- data.nodestab
|
||||||
|
|
||||||
|
'*_receiver':
|
||||||
|
- logstash
|
||||||
|
- logstash.receiver
|
||||||
|
- elasticsearch.auth
|
||||||
|
- global
|
||||||
|
- minions.{{ grains.id }}
|
||||||
|
|
||||||
|
'*_import':
|
||||||
|
- zeeklogs
|
||||||
|
- secrets
|
||||||
|
- elasticsearch.index_templates
|
||||||
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/elasticsearch/auth.sls') %}
|
||||||
|
- elasticsearch.auth
|
||||||
|
{% endif %}
|
||||||
|
{% if salt['file.file_exists']('/opt/so/saltstack/local/pillar/kibana/secrets.sls') %}
|
||||||
|
- kibana.secrets
|
||||||
|
{% endif %}
|
||||||
|
- global
|
||||||
|
- minions.{{ grains.id }}
|
||||||
|
|
||||||
|
'*_workstation':
|
||||||
- minions.{{ grains.id }}
|
- minions.{{ grains.id }}
|
||||||
- minions.adv_{{ grains.id }}
|
|
||||||
|
|||||||
@@ -1,2 +0,0 @@
|
|||||||
# users pillar goes in /opt/so/saltstack/local/pillar/users/init.sls
|
|
||||||
# the users directory may need to be created under /opt/so/saltstack/local/pillar
|
|
||||||
@@ -1,18 +0,0 @@
|
|||||||
users:
|
|
||||||
sclapton:
|
|
||||||
# required fields
|
|
||||||
status: present
|
|
||||||
# node_access determines which node types the user can access.
|
|
||||||
# this can either be by grains.role or by final part of the minion id after the _
|
|
||||||
node_access:
|
|
||||||
- standalone
|
|
||||||
- searchnode
|
|
||||||
# optional fields
|
|
||||||
fullname: Stevie Claptoon
|
|
||||||
uid: 1001
|
|
||||||
gid: 1001
|
|
||||||
homephone: does not have a phone
|
|
||||||
groups:
|
|
||||||
- mygroup1
|
|
||||||
- mygroup2
|
|
||||||
- wheel # give sudo access
|
|
||||||
@@ -1,20 +0,0 @@
|
|||||||
users:
|
|
||||||
sclapton:
|
|
||||||
# required fields
|
|
||||||
status: <present | absent>
|
|
||||||
# node_access determines which node types the user can access.
|
|
||||||
# this can either be by grains.role or by final part of the minion id after the _
|
|
||||||
node_access:
|
|
||||||
- standalone
|
|
||||||
- searchnode
|
|
||||||
# optional fields
|
|
||||||
fullname: <string>
|
|
||||||
uid: <integer>
|
|
||||||
gid: <integer>
|
|
||||||
roomnumber: <string>
|
|
||||||
workphone: <string>
|
|
||||||
homephone: <string>
|
|
||||||
groups:
|
|
||||||
- <string>
|
|
||||||
- <string>
|
|
||||||
- wheel # give sudo access
|
|
||||||
@@ -1 +1,55 @@
|
|||||||
zeek:
|
zeek:
|
||||||
|
zeekctl:
|
||||||
|
MailTo: root@localhost
|
||||||
|
MailConnectionSummary: 1
|
||||||
|
MinDiskSpace: 5
|
||||||
|
MailHostUpDown: 1
|
||||||
|
LogRotationInterval: 3600
|
||||||
|
LogExpireInterval: 0
|
||||||
|
StatsLogEnable: 1
|
||||||
|
StatsLogExpireInterval: 0
|
||||||
|
StatusCmdShowAll: 0
|
||||||
|
CrashExpireInterval: 0
|
||||||
|
SitePolicyScripts: local.zeek
|
||||||
|
LogDir: /nsm/zeek/logs
|
||||||
|
SpoolDir: /nsm/zeek/spool
|
||||||
|
CfgDir: /opt/zeek/etc
|
||||||
|
CompressLogs: 1
|
||||||
|
local:
|
||||||
|
'@load':
|
||||||
|
- misc/loaded-scripts
|
||||||
|
- tuning/defaults
|
||||||
|
- misc/capture-loss
|
||||||
|
- misc/stats
|
||||||
|
- frameworks/software/vulnerable
|
||||||
|
- frameworks/software/version-changes
|
||||||
|
- protocols/ftp/software
|
||||||
|
- protocols/smtp/software
|
||||||
|
- protocols/ssh/software
|
||||||
|
- protocols/http/software
|
||||||
|
- protocols/dns/detect-external-names
|
||||||
|
- protocols/ftp/detect
|
||||||
|
- protocols/conn/known-hosts
|
||||||
|
- protocols/conn/known-services
|
||||||
|
- protocols/ssl/known-certs
|
||||||
|
- protocols/ssl/validate-certs
|
||||||
|
- protocols/ssl/log-hostcerts-only
|
||||||
|
- protocols/ssh/geo-data
|
||||||
|
- protocols/ssh/detect-bruteforcing
|
||||||
|
- protocols/ssh/interesting-hostnames
|
||||||
|
- protocols/http/detect-sqli
|
||||||
|
- frameworks/files/hash-all-files
|
||||||
|
- frameworks/files/detect-MHR
|
||||||
|
- policy/frameworks/notice/extend-email/hostnames
|
||||||
|
- ja3
|
||||||
|
- hassh
|
||||||
|
- intel
|
||||||
|
- cve-2020-0601
|
||||||
|
- securityonion/bpfconf
|
||||||
|
- securityonion/communityid
|
||||||
|
- securityonion/file-extraction
|
||||||
|
'@load-sigs':
|
||||||
|
- frameworks/signatures/detect-windows-shells
|
||||||
|
redef:
|
||||||
|
- LogAscii::use_json = T;
|
||||||
|
- CaptureLoss::watch_interval = 5 mins;
|
||||||
|
|||||||
26
pyci.sh
@@ -1,26 +0,0 @@
|
|||||||
#!/bin/bash
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
|
||||||
# Elastic License 2.0.
|
|
||||||
|
|
||||||
if [[ $# -ne 1 ]]; then
|
|
||||||
echo "Usage: $0 <python_script_dir>"
|
|
||||||
echo "Runs tests on all *_test.py files in the given directory."
|
|
||||||
exit 1
|
|
||||||
fi
|
|
||||||
|
|
||||||
HOME_DIR=$(dirname "$0")
|
|
||||||
TARGET_DIR=${1:-.}
|
|
||||||
|
|
||||||
PATH=$PATH:/usr/local/bin
|
|
||||||
|
|
||||||
if ! which pytest &> /dev/null || ! which flake8 &> /dev/null ; then
|
|
||||||
echo "Missing dependencies. Consider running the following command:"
|
|
||||||
echo " python -m pip install flake8 pytest pytest-cov"
|
|
||||||
exit 1
|
|
||||||
fi
|
|
||||||
|
|
||||||
pip install pytest pytest-cov
|
|
||||||
flake8 "$TARGET_DIR" "--config=${HOME_DIR}/pytest.ini"
|
|
||||||
python3 -m pytest "--cov-config=${HOME_DIR}/pytest.ini" "--cov=$TARGET_DIR" --doctest-modules --cov-report=term --cov-fail-under=100 "$TARGET_DIR"
|
|
||||||
@@ -3,14 +3,14 @@ import subprocess
|
|||||||
|
|
||||||
def check():
|
def check():
|
||||||
|
|
||||||
osfam = __grains__['os_family']
|
os = __grains__['os']
|
||||||
retval = 'False'
|
retval = 'False'
|
||||||
|
|
||||||
if osfam == 'Debian':
|
if os == 'Ubuntu':
|
||||||
if path.exists('/var/run/reboot-required'):
|
if path.exists('/var/run/reboot-required'):
|
||||||
retval = 'True'
|
retval = 'True'
|
||||||
|
|
||||||
elif osfam == 'RedHat':
|
elif os == 'CentOS':
|
||||||
cmd = 'needs-restarting -r > /dev/null 2>&1'
|
cmd = 'needs-restarting -r > /dev/null 2>&1'
|
||||||
|
|
||||||
try:
|
try:
|
||||||
|
|||||||
@@ -5,8 +5,6 @@ import logging
|
|||||||
def status():
|
def status():
|
||||||
return __salt__['cmd.run']('/usr/sbin/so-status')
|
return __salt__['cmd.run']('/usr/sbin/so-status')
|
||||||
|
|
||||||
def version():
|
|
||||||
return __salt__['cp.get_file_str']('/etc/soversion')
|
|
||||||
|
|
||||||
def mysql_conn(retry):
|
def mysql_conn(retry):
|
||||||
log = logging.getLogger(__name__)
|
log = logging.getLogger(__name__)
|
||||||
@@ -63,4 +61,4 @@ def mysql_conn(retry):
|
|||||||
for addr in ip_arr:
|
for addr in ip_arr:
|
||||||
log.debug(f' - {addr}')
|
log.debug(f' - {addr}')
|
||||||
|
|
||||||
return mysql_up
|
return mysql_up
|
||||||
@@ -1,8 +1,18 @@
|
|||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
{% set ZEEKVER = salt['pillar.get']('global:mdengine', '') %}
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
{% set WAZUH = salt['pillar.get']('global:wazuh', '0') %}
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
{% set PLAYBOOK = salt['pillar.get']('manager:playbook', '0') %}
|
||||||
# Elastic License 2.0.
|
{% set FREQSERVER = salt['pillar.get']('manager:freq', '0') %}
|
||||||
|
{% set DOMAINSTATS = salt['pillar.get']('manager:domainstats', '0') %}
|
||||||
|
{% set FLEETMANAGER = salt['pillar.get']('global:fleet_manager', False) %}
|
||||||
|
{% set FLEETNODE = salt['pillar.get']('global:fleet_node', False) %}
|
||||||
|
{% set ELASTALERT = salt['pillar.get']('elastalert:enabled', True) %}
|
||||||
|
{% set ELASTICSEARCH = salt['pillar.get']('elasticsearch:enabled', True) %}
|
||||||
|
{% set FILEBEAT = salt['pillar.get']('filebeat:enabled', True) %}
|
||||||
|
{% set KIBANA = salt['pillar.get']('kibana:enabled', True) %}
|
||||||
|
{% set LOGSTASH = salt['pillar.get']('logstash:enabled', True) %}
|
||||||
|
{% set CURATOR = salt['pillar.get']('curator:enabled', True) %}
|
||||||
|
{% set REDIS = salt['pillar.get']('redis:enabled', True) %}
|
||||||
|
{% set STRELKA = salt['pillar.get']('strelka:enabled', '0') %}
|
||||||
{% set ISAIRGAP = salt['pillar.get']('global:airgap', False) %}
|
{% set ISAIRGAP = salt['pillar.get']('global:airgap', False) %}
|
||||||
{% import_yaml 'salt/minion.defaults.yaml' as saltversion %}
|
{% import_yaml 'salt/minion.defaults.yaml' as saltversion %}
|
||||||
{% set saltversion = saltversion.salt.minion.version %}
|
{% set saltversion = saltversion.salt.minion.version %}
|
||||||
@@ -22,10 +32,9 @@
|
|||||||
'nginx',
|
'nginx',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
'influxdb',
|
'influxdb',
|
||||||
|
'grafana',
|
||||||
'soc',
|
'soc',
|
||||||
'kratos',
|
'kratos',
|
||||||
'elasticfleet',
|
|
||||||
'elastic-fleet-package-registry',
|
|
||||||
'firewall',
|
'firewall',
|
||||||
'idstools',
|
'idstools',
|
||||||
'suricata.manager',
|
'suricata.manager',
|
||||||
@@ -36,7 +45,8 @@
|
|||||||
'schedule',
|
'schedule',
|
||||||
'soctopus',
|
'soctopus',
|
||||||
'tcpreplay',
|
'tcpreplay',
|
||||||
'docker_clean'
|
'docker_clean',
|
||||||
|
'learn'
|
||||||
],
|
],
|
||||||
'so-heavynode': [
|
'so-heavynode': [
|
||||||
'ssl',
|
'ssl',
|
||||||
@@ -46,15 +56,46 @@
|
|||||||
'pcap',
|
'pcap',
|
||||||
'suricata',
|
'suricata',
|
||||||
'healthcheck',
|
'healthcheck',
|
||||||
'elasticagent',
|
|
||||||
'schedule',
|
'schedule',
|
||||||
'tcpreplay',
|
'tcpreplay',
|
||||||
'docker_clean'
|
'docker_clean'
|
||||||
],
|
],
|
||||||
|
'so-helixsensor': [
|
||||||
|
'salt.master',
|
||||||
|
'ca',
|
||||||
|
'ssl',
|
||||||
|
'registry',
|
||||||
|
'telegraf',
|
||||||
|
'firewall',
|
||||||
|
'idstools',
|
||||||
|
'suricata.manager',
|
||||||
|
'zeek',
|
||||||
|
'redis',
|
||||||
|
'elasticsearch',
|
||||||
|
'logstash',
|
||||||
|
'schedule',
|
||||||
|
'tcpreplay',
|
||||||
|
'docker_clean'
|
||||||
|
],
|
||||||
|
'so-fleet': [
|
||||||
|
'ssl',
|
||||||
|
'nginx',
|
||||||
|
'telegraf',
|
||||||
|
'firewall',
|
||||||
|
'mysql',
|
||||||
|
'redis',
|
||||||
|
'fleet',
|
||||||
|
'fleet.install_package',
|
||||||
|
'filebeat',
|
||||||
|
'schedule',
|
||||||
|
'docker_clean'
|
||||||
|
],
|
||||||
'so-idh': [
|
'so-idh': [
|
||||||
'ssl',
|
'ssl',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
'firewall',
|
'firewall',
|
||||||
|
'fleet.install_package',
|
||||||
|
'filebeat',
|
||||||
'idh',
|
'idh',
|
||||||
'schedule',
|
'schedule',
|
||||||
'docker_clean'
|
'docker_clean'
|
||||||
@@ -68,8 +109,6 @@
|
|||||||
'nginx',
|
'nginx',
|
||||||
'soc',
|
'soc',
|
||||||
'kratos',
|
'kratos',
|
||||||
'influxdb',
|
|
||||||
'telegraf',
|
|
||||||
'firewall',
|
'firewall',
|
||||||
'idstools',
|
'idstools',
|
||||||
'suricata.manager',
|
'suricata.manager',
|
||||||
@@ -80,8 +119,7 @@
|
|||||||
'schedule',
|
'schedule',
|
||||||
'tcpreplay',
|
'tcpreplay',
|
||||||
'docker_clean',
|
'docker_clean',
|
||||||
'elasticfleet',
|
'learn'
|
||||||
'elastic-fleet-package-registry'
|
|
||||||
],
|
],
|
||||||
'so-manager': [
|
'so-manager': [
|
||||||
'salt.master',
|
'salt.master',
|
||||||
@@ -92,17 +130,17 @@
|
|||||||
'nginx',
|
'nginx',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
'influxdb',
|
'influxdb',
|
||||||
|
'grafana',
|
||||||
'soc',
|
'soc',
|
||||||
'kratos',
|
'kratos',
|
||||||
'elasticfleet',
|
|
||||||
'elastic-fleet-package-registry',
|
|
||||||
'firewall',
|
'firewall',
|
||||||
'idstools',
|
'idstools',
|
||||||
'suricata.manager',
|
'suricata.manager',
|
||||||
'utility',
|
'utility',
|
||||||
'schedule',
|
'schedule',
|
||||||
'soctopus',
|
'soctopus',
|
||||||
'docker_clean'
|
'docker_clean',
|
||||||
|
'learn'
|
||||||
],
|
],
|
||||||
'so-managersearch': [
|
'so-managersearch': [
|
||||||
'salt.master',
|
'salt.master',
|
||||||
@@ -112,10 +150,9 @@
|
|||||||
'nginx',
|
'nginx',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
'influxdb',
|
'influxdb',
|
||||||
|
'grafana',
|
||||||
'soc',
|
'soc',
|
||||||
'kratos',
|
'kratos',
|
||||||
'elastic-fleet-package-registry',
|
|
||||||
'elasticfleet',
|
|
||||||
'firewall',
|
'firewall',
|
||||||
'manager',
|
'manager',
|
||||||
'idstools',
|
'idstools',
|
||||||
@@ -123,9 +160,10 @@
|
|||||||
'utility',
|
'utility',
|
||||||
'schedule',
|
'schedule',
|
||||||
'soctopus',
|
'soctopus',
|
||||||
'docker_clean'
|
'docker_clean',
|
||||||
|
'learn'
|
||||||
],
|
],
|
||||||
'so-searchnode': [
|
'so-node': [
|
||||||
'ssl',
|
'ssl',
|
||||||
'nginx',
|
'nginx',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
@@ -142,10 +180,9 @@
|
|||||||
'nginx',
|
'nginx',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
'influxdb',
|
'influxdb',
|
||||||
|
'grafana',
|
||||||
'soc',
|
'soc',
|
||||||
'kratos',
|
'kratos',
|
||||||
'elastic-fleet-package-registry',
|
|
||||||
'elasticfleet',
|
|
||||||
'firewall',
|
'firewall',
|
||||||
'idstools',
|
'idstools',
|
||||||
'suricata.manager',
|
'suricata.manager',
|
||||||
@@ -156,7 +193,8 @@
|
|||||||
'schedule',
|
'schedule',
|
||||||
'soctopus',
|
'soctopus',
|
||||||
'tcpreplay',
|
'tcpreplay',
|
||||||
'docker_clean'
|
'docker_clean',
|
||||||
|
'learn'
|
||||||
],
|
],
|
||||||
'so-sensor': [
|
'so-sensor': [
|
||||||
'ssl',
|
'ssl',
|
||||||
@@ -166,20 +204,12 @@
|
|||||||
'pcap',
|
'pcap',
|
||||||
'suricata',
|
'suricata',
|
||||||
'healthcheck',
|
'healthcheck',
|
||||||
|
'wazuh',
|
||||||
|
'filebeat',
|
||||||
'schedule',
|
'schedule',
|
||||||
'tcpreplay',
|
'tcpreplay',
|
||||||
'docker_clean'
|
'docker_clean'
|
||||||
],
|
],
|
||||||
'so-fleet': [
|
|
||||||
'ssl',
|
|
||||||
'telegraf',
|
|
||||||
'firewall',
|
|
||||||
'logstash',
|
|
||||||
'healthcheck',
|
|
||||||
'schedule',
|
|
||||||
'elasticfleet',
|
|
||||||
'docker_clean'
|
|
||||||
],
|
|
||||||
'so-receiver': [
|
'so-receiver': [
|
||||||
'ssl',
|
'ssl',
|
||||||
'telegraf',
|
'telegraf',
|
||||||
@@ -187,54 +217,94 @@
|
|||||||
'schedule',
|
'schedule',
|
||||||
'docker_clean'
|
'docker_clean'
|
||||||
],
|
],
|
||||||
'so-desktop': [
|
'so-workstation': [
|
||||||
'ssl',
|
|
||||||
'docker_clean',
|
|
||||||
'telegraf'
|
|
||||||
],
|
],
|
||||||
}, grain='role') %}
|
}, grain='role') %}
|
||||||
|
|
||||||
{% if grains.role in ['so-eval', 'so-manager', 'so-managersearch', 'so-standalone'] %}
|
{% if FILEBEAT and grains.role in ['so-helixsensor', 'so-eval', 'so-manager', 'so-standalone', 'so-node', 'so-managersearch', 'so-heavynode', 'so-import', 'so-receiver'] %}
|
||||||
|
{% do allowed_states.append('filebeat') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if ((FLEETMANAGER or FLEETNODE) or PLAYBOOK != 0) and grains.role in ['so-eval', 'so-manager', 'so-managersearch', 'so-standalone'] %}
|
||||||
{% do allowed_states.append('mysql') %}
|
{% do allowed_states.append('mysql') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{%- if grains.role in ['so-sensor', 'so-eval', 'so-standalone', 'so-heavynode'] %}
|
{% if (FLEETMANAGER or FLEETNODE) and grains.role in ['so-sensor', 'so-eval', 'so-manager', 'so-standalone', 'so-node', 'so-managersearch', 'so-heavynode', 'so-receiver'] %}
|
||||||
|
{% do allowed_states.append('fleet.install_package') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if (FLEETMANAGER or FLEETNODE) and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-heavynode'] %}
|
||||||
|
{% do allowed_states.append('fleet') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if (FLEETMANAGER or FLEETNODE) and grains.role in ['so-eval'] %}
|
||||||
|
{% do allowed_states.append('redis') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{%- if ZEEKVER != 'SURICATA' and grains.role in ['so-sensor', 'so-eval', 'so-standalone', 'so-heavynode'] %}
|
||||||
{% do allowed_states.append('zeek') %}
|
{% do allowed_states.append('zeek') %}
|
||||||
{%- endif %}
|
{%- endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-sensor', 'so-eval', 'so-standalone', 'so-heavynode'] %}
|
{% if STRELKA and grains.role in ['so-sensor', 'so-eval', 'so-standalone', 'so-heavynode'] %}
|
||||||
{% do allowed_states.append('strelka') %}
|
{% do allowed_states.append('strelka') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-searchnode', 'so-managersearch', 'so-heavynode', 'so-import'] %}
|
{% if WAZUH and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-node', 'so-managersearch', 'so-heavynode', 'so-receiver','so-idh']%}
|
||||||
|
{% do allowed_states.append('wazuh') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if ELASTICSEARCH and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-node', 'so-managersearch', 'so-heavynode', 'so-import'] %}
|
||||||
{% do allowed_states.append('elasticsearch') %}
|
{% do allowed_states.append('elasticsearch') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-import'] %}
|
{% if ELASTICSEARCH and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-import'] %}
|
||||||
{% do allowed_states.append('elasticsearch.auth') %}
|
{% do allowed_states.append('elasticsearch.auth') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-import'] %}
|
{% if KIBANA and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-import'] %}
|
||||||
{% do allowed_states.append('kibana') %}
|
{% do allowed_states.append('kibana') %}
|
||||||
{% do allowed_states.append('kibana.secrets') %}
|
{% do allowed_states.append('kibana.secrets') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch'] %}
|
{% if grains.role in ['so-eval', 'so-standalone', 'so-node', 'so-managersearch', 'so-heavynode', 'so-manager'] %}
|
||||||
|
{% do allowed_states.append('curator') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if ELASTALERT and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch'] %}
|
||||||
{% do allowed_states.append('elastalert') %}
|
{% do allowed_states.append('elastalert') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch'] %}
|
{% if (PLAYBOOK !=0) and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch'] %}
|
||||||
{% do allowed_states.append('playbook') %}
|
{% do allowed_states.append('playbook') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-manager', 'so-standalone', 'so-searchnode', 'so-managersearch', 'so-heavynode', 'so-receiver'] %}
|
{% if (PLAYBOOK !=0) and grains.role in ['so-eval'] %}
|
||||||
|
{% do allowed_states.append('redis') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if (FREQSERVER !=0) and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch'] %}
|
||||||
|
{% do allowed_states.append('freqserver') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if (DOMAINSTATS !=0) and grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch'] %}
|
||||||
|
{% do allowed_states.append('domainstats') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
|
{% if LOGSTASH and grains.role in ['so-helixsensor', 'so-manager', 'so-standalone', 'so-node', 'so-managersearch', 'so-heavynode', 'so-receiver'] %}
|
||||||
{% do allowed_states.append('logstash') %}
|
{% do allowed_states.append('logstash') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if grains.role in ['so-manager', 'so-standalone', 'so-managersearch', 'so-heavynode', 'so-receiver', 'so-eval'] %}
|
{% if REDIS and grains.role in ['so-manager', 'so-standalone', 'so-managersearch', 'so-heavynode', 'so-receiver'] %}
|
||||||
{% do allowed_states.append('redis') %}
|
{% do allowed_states.append('redis') %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
|
{% if grains.os == 'CentOS' %}
|
||||||
|
{% if not ISAIRGAP %}
|
||||||
|
{% do allowed_states.append('yum') %}
|
||||||
|
{% endif %}
|
||||||
|
{% do allowed_states.append('yum.packages') %}
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
{# all nodes on the right salt version can run the following states #}
|
{# all nodes on the right salt version can run the following states #}
|
||||||
{% do allowed_states.append('common') %}
|
{% do allowed_states.append('common') %}
|
||||||
{% do allowed_states.append('patch.os.schedule') %}
|
{% do allowed_states.append('patch.os.schedule') %}
|
||||||
|
|||||||
@@ -1,34 +0,0 @@
|
|||||||
{% from 'backup/map.jinja' import BACKUP_MERGED %}
|
|
||||||
|
|
||||||
# Lock permissions on the backup directory
|
|
||||||
backupdir:
|
|
||||||
file.directory:
|
|
||||||
- name: /nsm/backup
|
|
||||||
- user: 0
|
|
||||||
- group: 0
|
|
||||||
- makedirs: True
|
|
||||||
- mode: 700
|
|
||||||
|
|
||||||
config_backup_script:
|
|
||||||
file.managed:
|
|
||||||
- name: /usr/sbin/so-config-backup
|
|
||||||
- user: root
|
|
||||||
- group: root
|
|
||||||
- mode: 755
|
|
||||||
- template: jinja
|
|
||||||
- source: salt://backup/tools/sbin/so-config-backup.jinja
|
|
||||||
- defaults:
|
|
||||||
BACKUPLOCATIONS: {{ BACKUP_MERGED.locations }}
|
|
||||||
DESTINATION: {{ BACKUP_MERGED.destination }}
|
|
||||||
|
|
||||||
# Add config backup
|
|
||||||
so_config_backup:
|
|
||||||
cron.present:
|
|
||||||
- name: /usr/sbin/so-config-backup > /dev/null 2>&1
|
|
||||||
- identifier: so_config_backup
|
|
||||||
- user: root
|
|
||||||
- minute: '1'
|
|
||||||
- hour: '0'
|
|
||||||
- daymonth: '*'
|
|
||||||
- month: '*'
|
|
||||||
- dayweek: '*'
|
|
||||||
@@ -1,7 +0,0 @@
|
|||||||
backup:
|
|
||||||
locations:
|
|
||||||
- /opt/so/saltstack/local
|
|
||||||
- /etc/pki
|
|
||||||
- /etc/salt
|
|
||||||
- /nsm/kratos
|
|
||||||
destination: "/nsm/backup"
|
|
||||||
@@ -1,2 +0,0 @@
|
|||||||
{% import_yaml 'backup/defaults.yaml' as BACKUP_DEFAULTS %}
|
|
||||||
{% set BACKUP_MERGED = salt['pillar.get']('backup', BACKUP_DEFAULTS.backup, merge=true, merge_nested_lists=true) %}
|
|
||||||
@@ -1,10 +0,0 @@
|
|||||||
backup:
|
|
||||||
locations:
|
|
||||||
description: List of locations to back up to the destination.
|
|
||||||
helpLink: backup.html
|
|
||||||
global: True
|
|
||||||
destination:
|
|
||||||
description: Directory to store the configuration backups in.
|
|
||||||
helpLink: backup.html
|
|
||||||
global: True
|
|
||||||
|
|
||||||
@@ -1,37 +0,0 @@
|
|||||||
#!/bin/bash
|
|
||||||
#
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
|
||||||
# Elastic License 2.0.
|
|
||||||
|
|
||||||
. /usr/sbin/so-common
|
|
||||||
|
|
||||||
TODAY=$(date '+%Y_%m_%d')
|
|
||||||
BACKUPDIR={{ DESTINATION }}
|
|
||||||
BACKUPFILE="$BACKUPDIR/so-config-backup-$TODAY.tar"
|
|
||||||
MAXBACKUPS=7
|
|
||||||
|
|
||||||
# Create backup dir if it does not exist
|
|
||||||
mkdir -p /nsm/backup
|
|
||||||
|
|
||||||
# If we haven't already written a backup file for today, let's do so
|
|
||||||
if [ ! -f $BACKUPFILE ]; then
|
|
||||||
|
|
||||||
# Create empty backup file
|
|
||||||
tar -cf $BACKUPFILE -T /dev/null
|
|
||||||
|
|
||||||
# Loop through all paths defined in global.sls, and append them to backup file
|
|
||||||
{%- for LOCATION in BACKUPLOCATIONS %}
|
|
||||||
tar -rf $BACKUPFILE {{ LOCATION }}
|
|
||||||
{%- endfor %}
|
|
||||||
|
|
||||||
fi
|
|
||||||
|
|
||||||
# Find oldest backup files and remove them
|
|
||||||
NUMBACKUPS=$(find /nsm/backup/ -type f -name "so-config-backup*" | wc -l)
|
|
||||||
while [ "$NUMBACKUPS" -gt "$MAXBACKUPS" ]; do
|
|
||||||
OLDESTBACKUP=$(find /nsm/backup/ -type f -name "so-config-backup*" -type f -printf '%T+ %p\n' | sort | head -n 1 | awk -F" " '{print $2}')
|
|
||||||
rm -f $OLDESTBACKUP
|
|
||||||
NUMBACKUPS=$(find /nsm/backup/ -type f -name "so-config-backup*" | wc -l)
|
|
||||||
done
|
|
||||||
@@ -1,4 +0,0 @@
|
|||||||
bpf:
|
|
||||||
pcap: []
|
|
||||||
suricata: []
|
|
||||||
zeek: []
|
|
||||||
@@ -1,10 +0,0 @@
|
|||||||
{% macro remove_comments(bpfmerged, app) %}
|
|
||||||
|
|
||||||
{# remove comments from the bpf #}
|
|
||||||
{% for bpf in bpfmerged[app] %}
|
|
||||||
{% if bpf.strip().startswith('#') %}
|
|
||||||
{% do bpfmerged[app].pop(loop.index0) %}
|
|
||||||
{% endif %}
|
|
||||||
{% endfor %}
|
|
||||||
|
|
||||||
{% endmacro %}
|
|
||||||
@@ -1,7 +0,0 @@
|
|||||||
{% import_yaml 'bpf/defaults.yaml' as BPFDEFAULTS %}
|
|
||||||
{% set BPFMERGED = salt['pillar.get']('bpf', BPFDEFAULTS.bpf, merge=True) %}
|
|
||||||
{% import 'bpf/macros.jinja' as MACROS %}
|
|
||||||
|
|
||||||
{{ MACROS.remove_comments(BPFMERGED, 'pcap') }}
|
|
||||||
|
|
||||||
{% set PCAPBPF = BPFMERGED.pcap %}
|
|
||||||
@@ -1,16 +0,0 @@
|
|||||||
bpf:
|
|
||||||
pcap:
|
|
||||||
description: List of BPF filters to apply to PCAP.
|
|
||||||
multiline: True
|
|
||||||
forcedType: "[]string"
|
|
||||||
helpLink: bpf.html
|
|
||||||
suricata:
|
|
||||||
description: List of BPF filters to apply to Suricata.
|
|
||||||
multiline: True
|
|
||||||
forcedType: "[]string"
|
|
||||||
helpLink: bpf.html
|
|
||||||
zeek:
|
|
||||||
description: List of BPF filters to apply to Zeek.
|
|
||||||
multiline: True
|
|
||||||
forcedType: "[]string"
|
|
||||||
helpLink: bpf.html
|
|
||||||
@@ -1,7 +0,0 @@
|
|||||||
{% import_yaml 'bpf/defaults.yaml' as BPFDEFAULTS %}
|
|
||||||
{% set BPFMERGED = salt['pillar.get']('bpf', BPFDEFAULTS.bpf, merge=True) %}
|
|
||||||
{% import 'bpf/macros.jinja' as MACROS %}
|
|
||||||
|
|
||||||
{{ MACROS.remove_comments(BPFMERGED, 'suricata') }}
|
|
||||||
|
|
||||||
{% set SURICATABPF = BPFMERGED.suricata %}
|
|
||||||
@@ -1,7 +0,0 @@
|
|||||||
{% import_yaml 'bpf/defaults.yaml' as BPFDEFAULTS %}
|
|
||||||
{% set BPFMERGED = salt['pillar.get']('bpf', BPFDEFAULTS.bpf, merge=True) %}
|
|
||||||
{% import 'bpf/macros.jinja' as MACROS %}
|
|
||||||
|
|
||||||
{{ MACROS.remove_comments(BPFMERGED, 'zeek') }}
|
|
||||||
|
|
||||||
{% set ZEEKBPF = BPFMERGED.zeek %}
|
|
||||||
@@ -37,7 +37,7 @@ x509_signing_policies:
|
|||||||
- ST: Utah
|
- ST: Utah
|
||||||
- L: Salt Lake City
|
- L: Salt Lake City
|
||||||
- basicConstraints: "critical CA:false"
|
- basicConstraints: "critical CA:false"
|
||||||
- keyUsage: "critical keyEncipherment digitalSignature"
|
- keyUsage: "critical keyEncipherment"
|
||||||
- subjectKeyIdentifier: hash
|
- subjectKeyIdentifier: hash
|
||||||
- authorityKeyIdentifier: keyid,issuer:always
|
- authorityKeyIdentifier: keyid,issuer:always
|
||||||
- extendedKeyUsage: serverAuth
|
- extendedKeyUsage: serverAuth
|
||||||
@@ -57,7 +57,7 @@ x509_signing_policies:
|
|||||||
- extendedKeyUsage: serverAuth
|
- extendedKeyUsage: serverAuth
|
||||||
- days_valid: 820
|
- days_valid: 820
|
||||||
- copypath: /etc/pki/issued_certs/
|
- copypath: /etc/pki/issued_certs/
|
||||||
elasticfleet:
|
fleet:
|
||||||
- minions: '*'
|
- minions: '*'
|
||||||
- signing_private_key: /etc/pki/ca.key
|
- signing_private_key: /etc/pki/ca.key
|
||||||
- signing_cert: /etc/pki/ca.crt
|
- signing_cert: /etc/pki/ca.crt
|
||||||
@@ -65,8 +65,9 @@ x509_signing_policies:
|
|||||||
- ST: Utah
|
- ST: Utah
|
||||||
- L: Salt Lake City
|
- L: Salt Lake City
|
||||||
- basicConstraints: "critical CA:false"
|
- basicConstraints: "critical CA:false"
|
||||||
- keyUsage: "digitalSignature, nonRepudiation"
|
- keyUsage: "critical keyEncipherment"
|
||||||
- subjectKeyIdentifier: hash
|
- subjectKeyIdentifier: hash
|
||||||
- authorityKeyIdentifier: keyid,issuer:always
|
- authorityKeyIdentifier: keyid,issuer:always
|
||||||
|
- extendedKeyUsage: serverAuth
|
||||||
- days_valid: 820
|
- days_valid: 820
|
||||||
- copypath: /etc/pki/issued_certs/
|
- copypath: /etc/pki/issued_certs/
|
||||||
|
|||||||
@@ -1,16 +1,10 @@
|
|||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
|
||||||
# Elastic License 2.0.
|
|
||||||
|
|
||||||
{% from 'allowed_states.map.jinja' import allowed_states %}
|
{% from 'allowed_states.map.jinja' import allowed_states %}
|
||||||
{% if sls in allowed_states %}
|
{% if sls in allowed_states %}
|
||||||
{% from 'vars/globals.map.jinja' import GLOBALS %}
|
|
||||||
|
|
||||||
|
|
||||||
include:
|
include:
|
||||||
- ca.dirs
|
- ca.dirs
|
||||||
|
|
||||||
|
{% set manager = salt['grains.get']('master') %}
|
||||||
/etc/salt/minion.d/signing_policies.conf:
|
/etc/salt/minion.d/signing_policies.conf:
|
||||||
file.managed:
|
file.managed:
|
||||||
- source: salt://ca/files/signing_policies.conf
|
- source: salt://ca/files/signing_policies.conf
|
||||||
@@ -18,8 +12,9 @@ include:
|
|||||||
pki_private_key:
|
pki_private_key:
|
||||||
x509.private_key_managed:
|
x509.private_key_managed:
|
||||||
- name: /etc/pki/ca.key
|
- name: /etc/pki/ca.key
|
||||||
- keysize: 4096
|
- bits: 4096
|
||||||
- passphrase:
|
- passphrase:
|
||||||
|
- cipher: aes_256_cbc
|
||||||
- backup: True
|
- backup: True
|
||||||
{% if salt['file.file_exists']('/etc/pki/ca.key') -%}
|
{% if salt['file.file_exists']('/etc/pki/ca.key') -%}
|
||||||
- prereq:
|
- prereq:
|
||||||
@@ -30,7 +25,7 @@ pki_public_ca_crt:
|
|||||||
x509.certificate_managed:
|
x509.certificate_managed:
|
||||||
- name: /etc/pki/ca.crt
|
- name: /etc/pki/ca.crt
|
||||||
- signing_private_key: /etc/pki/ca.key
|
- signing_private_key: /etc/pki/ca.key
|
||||||
- CN: {{ GLOBALS.manager }}
|
- CN: {{ manager }}
|
||||||
- C: US
|
- C: US
|
||||||
- ST: Utah
|
- ST: Utah
|
||||||
- L: Salt Lake City
|
- L: Salt Lake City
|
||||||
@@ -38,7 +33,7 @@ pki_public_ca_crt:
|
|||||||
- keyUsage: "critical cRLSign, keyCertSign"
|
- keyUsage: "critical cRLSign, keyCertSign"
|
||||||
- extendedkeyUsage: "serverAuth, clientAuth"
|
- extendedkeyUsage: "serverAuth, clientAuth"
|
||||||
- subjectKeyIdentifier: hash
|
- subjectKeyIdentifier: hash
|
||||||
- authorityKeyIdentifier: keyid:always, issuer
|
- authorityKeyIdentifier: keyid,issuer:always
|
||||||
- days_valid: 3650
|
- days_valid: 3650
|
||||||
- days_remaining: 0
|
- days_remaining: 0
|
||||||
- backup: True
|
- backup: True
|
||||||
@@ -50,12 +45,6 @@ pki_public_ca_crt:
|
|||||||
attempts: 5
|
attempts: 5
|
||||||
interval: 30
|
interval: 30
|
||||||
|
|
||||||
mine_update_ca_crt:
|
|
||||||
module.run:
|
|
||||||
- mine.update: []
|
|
||||||
- onchanges:
|
|
||||||
- x509: pki_public_ca_crt
|
|
||||||
|
|
||||||
cakeyperms:
|
cakeyperms:
|
||||||
file.managed:
|
file.managed:
|
||||||
- replace: False
|
- replace: False
|
||||||
|
|||||||
2
salt/common/cron/common-rotate
Normal file
@@ -0,0 +1,2 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
/usr/sbin/logrotate -f /opt/so/conf/log-rotate.conf > /dev/null 2>&1
|
||||||
2
salt/common/cron/sensor-rotate
Normal file
@@ -0,0 +1,2 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
/usr/sbin/logrotate -f /opt/so/conf/sensor-rotate.conf > /dev/null 2>&1
|
||||||
79
salt/common/files/analyst/README
Normal file
@@ -0,0 +1,79 @@
|
|||||||
|
The following GUI tools are available on the analyst workstation:
|
||||||
|
|
||||||
|
chromium
|
||||||
|
url: https://www.chromium.org/Home
|
||||||
|
To run chromium, click Applications > Internet > Chromium Web Browser
|
||||||
|
|
||||||
|
Wireshark
|
||||||
|
url: https://www.wireshark.org/
|
||||||
|
To run Wireshark, click Applications > Internet > Wireshark Network Analyzer
|
||||||
|
|
||||||
|
NetworkMiner
|
||||||
|
url: https://www.netresec.com
|
||||||
|
To run NetworkMiner, click Applications > Internet > NetworkMiner
|
||||||
|
|
||||||
|
The following CLI tools are available on the analyst workstation:
|
||||||
|
|
||||||
|
bit-twist
|
||||||
|
url: http://bittwist.sourceforge.net
|
||||||
|
To run bit-twist, open a terminal and type: bittwist -h
|
||||||
|
|
||||||
|
chaosreader
|
||||||
|
url: http://chaosreader.sourceforge.net
|
||||||
|
To run chaosreader, open a terminal and type: chaosreader -h
|
||||||
|
|
||||||
|
dnsiff
|
||||||
|
url: https://www.monkey.org/~dugsong/dsniff/
|
||||||
|
To run dsniff, open a terminal and type: dsniff -h
|
||||||
|
|
||||||
|
foremost
|
||||||
|
url: http://foremost.sourceforge.net
|
||||||
|
To run foremost, open a terminal and type: foremost -h
|
||||||
|
|
||||||
|
hping3
|
||||||
|
url: http://www.hping.org/hping3.html
|
||||||
|
To run hping3, open a terminal and type: hping3 -h
|
||||||
|
|
||||||
|
netsed
|
||||||
|
url: http://silicone.homelinux.org/projects/netsed/
|
||||||
|
To run netsed, open a terminal and type: netsed -h
|
||||||
|
|
||||||
|
ngrep
|
||||||
|
url: https://github.com/jpr5/ngrep
|
||||||
|
To run ngrep, open a terminal and type: ngrep -h
|
||||||
|
|
||||||
|
scapy
|
||||||
|
url: http://www.secdev.org/projects/scapy/
|
||||||
|
To run scapy, open a terminal and type: scapy
|
||||||
|
|
||||||
|
ssldump
|
||||||
|
url: http://www.rtfm.com/ssldump/
|
||||||
|
To run ssldump, open a terminal and type: ssldump -h
|
||||||
|
|
||||||
|
sslsplit
|
||||||
|
url: https://github.com/droe/sslsplit
|
||||||
|
To run sslsplit, open a terminal and type: sslsplit -h
|
||||||
|
|
||||||
|
tcpdump
|
||||||
|
url: http://www.tcpdump.org
|
||||||
|
To run tcpdump, open a terminal and type: tcpdump -h
|
||||||
|
|
||||||
|
tcpflow
|
||||||
|
url: https://github.com/simsong/tcpflow
|
||||||
|
To run tcpflow, open a terminal and type: tcpflow -h
|
||||||
|
|
||||||
|
tcpstat
|
||||||
|
url: https://frenchfries.net/paul/tcpstat/
|
||||||
|
To run tcpstat, open a terminal and type: tcpstat -h
|
||||||
|
|
||||||
|
tcptrace
|
||||||
|
url: http://www.tcptrace.org
|
||||||
|
To run tcptrace, open a terminal and type: tcptrace -h
|
||||||
|
|
||||||
|
tcpxtract
|
||||||
|
url: http://tcpxtract.sourceforge.net/
|
||||||
|
To run tcpxtract, open a terminal and type: tcpxtract -h
|
||||||
|
|
||||||
|
whois
|
||||||
|
url: http://www.linux.it/~md/software/
|
||||||
|
To run whois, open a terminal and type: whois -h
|
||||||
|
Before Width: | Height: | Size: 269 KiB After Width: | Height: | Size: 269 KiB |
|
Before Width: | Height: | Size: 1.7 KiB After Width: | Height: | Size: 1.7 KiB |
|
Before Width: | Height: | Size: 1.7 KiB After Width: | Height: | Size: 1.7 KiB |
|
Before Width: | Height: | Size: 319 KiB After Width: | Height: | Size: 319 KiB |
@@ -1,12 +1,12 @@
|
|||||||
|
{%- set DOCKERRANGE = salt['pillar.get']('docker:range', '172.17.0.0/24') %}
|
||||||
|
{%- set DOCKERBIND = salt['pillar.get']('docker:bip', '172.17.0.1/24') %}
|
||||||
{
|
{
|
||||||
"registry-mirrors": [
|
"registry-mirrors": [ "https://:5000" ],
|
||||||
"https://:5000"
|
"bip": "{{ DOCKERBIND }}",
|
||||||
],
|
"default-address-pools": [
|
||||||
"bip": "172.17.0.1/24",
|
{
|
||||||
"default-address-pools": [
|
"base" : "{{ DOCKERRANGE }}",
|
||||||
{
|
"size" : 24
|
||||||
"base": "172.17.0.0/24",
|
}
|
||||||
"size": 24
|
]
|
||||||
}
|
|
||||||
]
|
|
||||||
}
|
}
|
||||||
|
|||||||
37
salt/common/files/log-rotate.conf
Normal file
@@ -0,0 +1,37 @@
|
|||||||
|
{%- set logrotate_conf = salt['pillar.get']('logrotate:conf') %}
|
||||||
|
{%- set group_conf = salt['pillar.get']('logrotate:group_conf') %}
|
||||||
|
|
||||||
|
|
||||||
|
/opt/so/log/aptcacher-ng/*.log
|
||||||
|
/opt/so/log/idstools/*.log
|
||||||
|
/opt/so/log/nginx/*.log
|
||||||
|
/opt/so/log/soc/*.log
|
||||||
|
/opt/so/log/kratos/*.log
|
||||||
|
/opt/so/log/kibana/*.log
|
||||||
|
/opt/so/log/influxdb/*.log
|
||||||
|
/opt/so/log/elastalert/*.log
|
||||||
|
/opt/so/log/soctopus/*.log
|
||||||
|
/opt/so/log/curator/*.log
|
||||||
|
/opt/so/log/fleet/*.log
|
||||||
|
/opt/so/log/suricata/*.log
|
||||||
|
/opt/so/log/mysql/*.log
|
||||||
|
/opt/so/log/telegraf/*.log
|
||||||
|
/opt/so/log/redis/*.log
|
||||||
|
/opt/so/log/sensoroni/*.log
|
||||||
|
/opt/so/log/stenographer/*.log
|
||||||
|
/opt/so/log/salt/so-salt-minion-check
|
||||||
|
/opt/so/log/salt/minion
|
||||||
|
/opt/so/log/salt/master
|
||||||
|
/opt/so/log/logscan/*.log
|
||||||
|
/nsm/idh/*.log
|
||||||
|
{
|
||||||
|
{{ logrotate_conf | indent(width=4) }}
|
||||||
|
}
|
||||||
|
|
||||||
|
# Playbook's log directory needs additional configuration
|
||||||
|
# because Playbook requires a more permissive directory
|
||||||
|
/opt/so/log/playbook/*.log
|
||||||
|
{
|
||||||
|
{{ logrotate_conf | indent(width=4) }}
|
||||||
|
{{ group_conf | indent(width=4) }}
|
||||||
|
}
|
||||||
22
salt/common/files/sensor-rotate.conf
Normal file
@@ -0,0 +1,22 @@
|
|||||||
|
/opt/so/log/sensor_clean.log
|
||||||
|
{
|
||||||
|
daily
|
||||||
|
rotate 2
|
||||||
|
missingok
|
||||||
|
nocompress
|
||||||
|
create
|
||||||
|
sharedscripts
|
||||||
|
}
|
||||||
|
|
||||||
|
/nsm/strelka/log/strelka.log
|
||||||
|
{
|
||||||
|
daily
|
||||||
|
rotate 14
|
||||||
|
missingok
|
||||||
|
copytruncate
|
||||||
|
compress
|
||||||
|
create
|
||||||
|
extension .log
|
||||||
|
dateext
|
||||||
|
dateyesterday
|
||||||
|
}
|
||||||
@@ -3,3 +3,4 @@ filetype plugin indent on
|
|||||||
|
|
||||||
" Sets .sls files to use YAML syntax highlighting
|
" Sets .sls files to use YAML syntax highlighting
|
||||||
autocmd BufNewFile,BufRead *.sls set syntax=yaml
|
autocmd BufNewFile,BufRead *.sls set syntax=yaml
|
||||||
|
set number
|
||||||
@@ -1,25 +1,25 @@
|
|||||||
{% from 'allowed_states.map.jinja' import allowed_states %}
|
{% from 'allowed_states.map.jinja' import allowed_states %}
|
||||||
{% if sls in allowed_states %}
|
{% if sls in allowed_states %}
|
||||||
|
|
||||||
{% from 'vars/globals.map.jinja' import GLOBALS %}
|
{% set role = grains.id.split('_') | last %}
|
||||||
|
{% from 'elasticsearch/auth.map.jinja' import ELASTICAUTH with context %}
|
||||||
|
|
||||||
include:
|
include:
|
||||||
- common.soup_scripts
|
- common.soup_scripts
|
||||||
- common.packages
|
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-import'] %}
|
||||||
{% if GLOBALS.role in GLOBALS.manager_roles %}
|
|
||||||
- manager.elasticsearch # needed for elastic_curl_config state
|
- manager.elasticsearch # needed for elastic_curl_config state
|
||||||
- manager.kibana
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
net.core.wmem_default:
|
|
||||||
sysctl.present:
|
|
||||||
- value: 26214400
|
|
||||||
|
|
||||||
# Remove variables.txt from /tmp - This is temp
|
# Remove variables.txt from /tmp - This is temp
|
||||||
rmvariablesfile:
|
rmvariablesfile:
|
||||||
file.absent:
|
file.absent:
|
||||||
- name: /tmp/variables.txt
|
- name: /tmp/variables.txt
|
||||||
|
|
||||||
|
dockergroup:
|
||||||
|
group.present:
|
||||||
|
- name: docker
|
||||||
|
- gid: 920
|
||||||
|
|
||||||
# Add socore Group
|
# Add socore Group
|
||||||
socoregroup:
|
socoregroup:
|
||||||
group.present:
|
group.present:
|
||||||
@@ -38,15 +38,15 @@ socore:
|
|||||||
soconfperms:
|
soconfperms:
|
||||||
file.directory:
|
file.directory:
|
||||||
- name: /opt/so/conf
|
- name: /opt/so/conf
|
||||||
- user: 939
|
- uid: 939
|
||||||
- group: 939
|
- gid: 939
|
||||||
- dir_mode: 770
|
- dir_mode: 770
|
||||||
|
|
||||||
sostatusconf:
|
sostatusconf:
|
||||||
file.directory:
|
file.directory:
|
||||||
- name: /opt/so/conf/so-status
|
- name: /opt/so/conf/so-status
|
||||||
- user: 939
|
- uid: 939
|
||||||
- group: 939
|
- gid: 939
|
||||||
- dir_mode: 770
|
- dir_mode: 770
|
||||||
|
|
||||||
so-status.conf:
|
so-status.conf:
|
||||||
@@ -54,12 +54,13 @@ so-status.conf:
|
|||||||
- name: /opt/so/conf/so-status/so-status.conf
|
- name: /opt/so/conf/so-status/so-status.conf
|
||||||
- unless: ls /opt/so/conf/so-status/so-status.conf
|
- unless: ls /opt/so/conf/so-status/so-status.conf
|
||||||
|
|
||||||
socore_opso_perms:
|
sosaltstackperms:
|
||||||
file.directory:
|
file.directory:
|
||||||
- name: /opt/so
|
- name: /opt/so/saltstack
|
||||||
- user: 939
|
- uid: 939
|
||||||
- group: 939
|
- gid: 939
|
||||||
|
- dir_mode: 770
|
||||||
|
|
||||||
so_log_perms:
|
so_log_perms:
|
||||||
file.directory:
|
file.directory:
|
||||||
- name: /opt/so/log
|
- name: /opt/so/log
|
||||||
@@ -87,6 +88,92 @@ vimconfig:
|
|||||||
- source: salt://common/files/vimrc
|
- source: salt://common/files/vimrc
|
||||||
- replace: False
|
- replace: False
|
||||||
|
|
||||||
|
# Install common packages
|
||||||
|
{% if grains['os'] != 'CentOS' %}
|
||||||
|
commonpkgs:
|
||||||
|
pkg.installed:
|
||||||
|
- skip_suggestions: True
|
||||||
|
- pkgs:
|
||||||
|
- apache2-utils
|
||||||
|
- wget
|
||||||
|
- ntpdate
|
||||||
|
- jq
|
||||||
|
- python3-docker
|
||||||
|
- curl
|
||||||
|
- ca-certificates
|
||||||
|
- software-properties-common
|
||||||
|
- apt-transport-https
|
||||||
|
- openssl
|
||||||
|
- netcat
|
||||||
|
- python3-mysqldb
|
||||||
|
- sqlite3
|
||||||
|
- libssl-dev
|
||||||
|
- python3-dateutil
|
||||||
|
- python3-m2crypto
|
||||||
|
- python3-mysqldb
|
||||||
|
- python3-packaging
|
||||||
|
- python3-lxml
|
||||||
|
- git
|
||||||
|
- vim
|
||||||
|
|
||||||
|
heldpackages:
|
||||||
|
pkg.installed:
|
||||||
|
- pkgs:
|
||||||
|
{% if grains['oscodename'] == 'bionic' %}
|
||||||
|
- containerd.io: 1.4.4-1
|
||||||
|
- docker-ce: 5:20.10.5~3-0~ubuntu-bionic
|
||||||
|
- docker-ce-cli: 5:20.10.5~3-0~ubuntu-bionic
|
||||||
|
- docker-ce-rootless-extras: 5:20.10.5~3-0~ubuntu-bionic
|
||||||
|
{% elif grains['oscodename'] == 'focal' %}
|
||||||
|
- containerd.io: 1.4.9-1
|
||||||
|
- docker-ce: 5:20.10.8~3-0~ubuntu-focal
|
||||||
|
- docker-ce-cli: 5:20.10.5~3-0~ubuntu-focal
|
||||||
|
- docker-ce-rootless-extras: 5:20.10.5~3-0~ubuntu-focal
|
||||||
|
{% endif %}
|
||||||
|
- hold: True
|
||||||
|
- update_holds: True
|
||||||
|
|
||||||
|
{% else %}
|
||||||
|
commonpkgs:
|
||||||
|
pkg.installed:
|
||||||
|
- skip_suggestions: True
|
||||||
|
- pkgs:
|
||||||
|
- wget
|
||||||
|
- ntpdate
|
||||||
|
- bind-utils
|
||||||
|
- jq
|
||||||
|
- tcpdump
|
||||||
|
- httpd-tools
|
||||||
|
- net-tools
|
||||||
|
- curl
|
||||||
|
- sqlite
|
||||||
|
- mariadb-devel
|
||||||
|
- nmap-ncat
|
||||||
|
- python3
|
||||||
|
- python36-docker
|
||||||
|
- python36-dateutil
|
||||||
|
- python36-m2crypto
|
||||||
|
- python36-mysql
|
||||||
|
- python36-packaging
|
||||||
|
- python36-lxml
|
||||||
|
- yum-utils
|
||||||
|
- device-mapper-persistent-data
|
||||||
|
- lvm2
|
||||||
|
- openssl
|
||||||
|
- git
|
||||||
|
- vim-enhanced
|
||||||
|
|
||||||
|
heldpackages:
|
||||||
|
pkg.installed:
|
||||||
|
- pkgs:
|
||||||
|
- containerd.io: 1.4.4-3.1.el7
|
||||||
|
- docker-ce: 3:20.10.5-3.el7
|
||||||
|
- docker-ce-cli: 1:20.10.5-3.el7
|
||||||
|
- docker-ce-rootless-extras: 20.10.5-3.el7
|
||||||
|
- hold: True
|
||||||
|
- update_holds: True
|
||||||
|
{% endif %}
|
||||||
|
|
||||||
# Always keep these packages up to date
|
# Always keep these packages up to date
|
||||||
|
|
||||||
alwaysupdated:
|
alwaysupdated:
|
||||||
@@ -101,8 +188,7 @@ alwaysupdated:
|
|||||||
Etc/UTC:
|
Etc/UTC:
|
||||||
timezone.system
|
timezone.system
|
||||||
|
|
||||||
# Sync curl configuration for Elasticsearch authentication
|
{% if salt['pillar.get']('elasticsearch:auth:enabled', False) %}
|
||||||
{% if GLOBALS.role in ['so-eval', 'so-heavynode', 'so-import', 'so-manager', 'so-managersearch', 'so-searchnode', 'so-standalone'] %}
|
|
||||||
elastic_curl_config:
|
elastic_curl_config:
|
||||||
file.managed:
|
file.managed:
|
||||||
- name: /opt/so/conf/elasticsearch/curl.config
|
- name: /opt/so/conf/elasticsearch/curl.config
|
||||||
@@ -110,50 +196,87 @@ elastic_curl_config:
|
|||||||
- mode: 600
|
- mode: 600
|
||||||
- show_changes: False
|
- show_changes: False
|
||||||
- makedirs: True
|
- makedirs: True
|
||||||
{% if GLOBALS.role in GLOBALS.manager_roles %}
|
{% if grains.role in ['so-eval', 'so-manager', 'so-standalone', 'so-managersearch', 'so-import'] %}
|
||||||
- require:
|
- require:
|
||||||
- file: elastic_curl_config_distributed
|
- file: elastic_curl_config_distributed
|
||||||
{% endif %}
|
{% endif %}
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
|
# Sync some Utilities
|
||||||
common_sbin:
|
utilsyncscripts:
|
||||||
file.recurse:
|
file.recurse:
|
||||||
- name: /usr/sbin
|
- name: /usr/sbin
|
||||||
- source: salt://common/tools/sbin
|
- user: root
|
||||||
- user: 939
|
- group: root
|
||||||
- group: 939
|
|
||||||
- file_mode: 755
|
|
||||||
|
|
||||||
common_sbin_jinja:
|
|
||||||
file.recurse:
|
|
||||||
- name: /usr/sbin
|
|
||||||
- source: salt://common/tools/sbin_jinja
|
|
||||||
- user: 939
|
|
||||||
- group: 939
|
|
||||||
- file_mode: 755
|
- file_mode: 755
|
||||||
- template: jinja
|
- template: jinja
|
||||||
|
- source: salt://common/tools/sbin
|
||||||
|
- defaults:
|
||||||
|
ELASTICCURL: 'curl'
|
||||||
|
- context:
|
||||||
|
ELASTICCURL: {{ ELASTICAUTH.elasticcurl }}
|
||||||
|
- exclude_pat:
|
||||||
|
- so-common
|
||||||
|
- so-firewall
|
||||||
|
- so-image-common
|
||||||
|
- soup
|
||||||
|
|
||||||
so-status_script:
|
{% if role in ['eval', 'standalone', 'sensor', 'heavynode'] %}
|
||||||
file.managed:
|
|
||||||
- name: /usr/sbin/so-status
|
|
||||||
- source: salt://common/tools/sbin/so-status
|
|
||||||
- mode: 755
|
|
||||||
|
|
||||||
{% if GLOBALS.role in GLOBALS.sensor_roles %}
|
|
||||||
# Add sensor cleanup
|
# Add sensor cleanup
|
||||||
so-sensor-clean:
|
/usr/sbin/so-sensor-clean:
|
||||||
cron.present:
|
cron.present:
|
||||||
- name: /usr/sbin/so-sensor-clean
|
|
||||||
- identifier: so-sensor-clean
|
|
||||||
- user: root
|
- user: root
|
||||||
- minute: '*'
|
- minute: '*'
|
||||||
- hour: '*'
|
- hour: '*'
|
||||||
- daymonth: '*'
|
- daymonth: '*'
|
||||||
- month: '*'
|
- month: '*'
|
||||||
- dayweek: '*'
|
- dayweek: '*'
|
||||||
|
|
||||||
|
sensorrotatescript:
|
||||||
|
file.managed:
|
||||||
|
- name: /usr/local/bin/sensor-rotate
|
||||||
|
- source: salt://common/cron/sensor-rotate
|
||||||
|
- mode: 755
|
||||||
|
|
||||||
|
sensorrotateconf:
|
||||||
|
file.managed:
|
||||||
|
- name: /opt/so/conf/sensor-rotate.conf
|
||||||
|
- source: salt://common/files/sensor-rotate.conf
|
||||||
|
- mode: 644
|
||||||
|
|
||||||
|
/usr/local/bin/sensor-rotate:
|
||||||
|
cron.present:
|
||||||
|
- user: root
|
||||||
|
- minute: '1'
|
||||||
|
- hour: '0'
|
||||||
|
- daymonth: '*'
|
||||||
|
- month: '*'
|
||||||
|
- dayweek: '*'
|
||||||
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
|
commonlogrotatescript:
|
||||||
|
file.managed:
|
||||||
|
- name: /usr/local/bin/common-rotate
|
||||||
|
- source: salt://common/cron/common-rotate
|
||||||
|
- mode: 755
|
||||||
|
|
||||||
|
commonlogrotateconf:
|
||||||
|
file.managed:
|
||||||
|
- name: /opt/so/conf/log-rotate.conf
|
||||||
|
- source: salt://common/files/log-rotate.conf
|
||||||
|
- template: jinja
|
||||||
|
- mode: 644
|
||||||
|
|
||||||
|
/usr/local/bin/common-rotate:
|
||||||
|
cron.present:
|
||||||
|
- user: root
|
||||||
|
- minute: '1'
|
||||||
|
- hour: '0'
|
||||||
|
- daymonth: '*'
|
||||||
|
- month: '*'
|
||||||
|
- dayweek: '*'
|
||||||
|
|
||||||
# Create the status directory
|
# Create the status directory
|
||||||
sostatusdir:
|
sostatusdir:
|
||||||
file.directory:
|
file.directory:
|
||||||
@@ -166,12 +289,10 @@ sostatus_log:
|
|||||||
file.managed:
|
file.managed:
|
||||||
- name: /opt/so/log/sostatus/status.log
|
- name: /opt/so/log/sostatus/status.log
|
||||||
- mode: 644
|
- mode: 644
|
||||||
|
|
||||||
# Install sostatus check cron. This is used to populate Grid.
|
# Install sostatus check cron
|
||||||
so-status_check_cron:
|
'/usr/sbin/so-status -q; echo $? > /opt/so/log/sostatus/status.log 2>&1':
|
||||||
cron.present:
|
cron.present:
|
||||||
- name: '/usr/sbin/so-status -j > /opt/so/log/sostatus/status.log 2>&1'
|
|
||||||
- identifier: so-status_check_cron
|
|
||||||
- user: root
|
- user: root
|
||||||
- minute: '*/1'
|
- minute: '*/1'
|
||||||
- hour: '*'
|
- hour: '*'
|
||||||
@@ -179,21 +300,36 @@ so-status_check_cron:
|
|||||||
- month: '*'
|
- month: '*'
|
||||||
- dayweek: '*'
|
- dayweek: '*'
|
||||||
|
|
||||||
# This cronjob/script runs a check if the node needs restarted, but should be used for future status checks as well
|
{% if role in ['eval', 'manager', 'managersearch', 'standalone'] %}
|
||||||
common_status_check_cron:
|
# Install cron job to determine size of influxdb for telegraf
|
||||||
|
'du -s -k /nsm/influxdb | cut -f1 > /opt/so/log/telegraf/influxdb_size.log 2>&1':
|
||||||
cron.present:
|
cron.present:
|
||||||
- name: '/usr/sbin/so-common-status-check > /dev/null 2>&1'
|
|
||||||
- identifier: common_status_check
|
|
||||||
- user: root
|
- user: root
|
||||||
- minute: '*/10'
|
- minute: '*/1'
|
||||||
|
- hour: '*'
|
||||||
remove_post_setup_cron:
|
- daymonth: '*'
|
||||||
cron.absent:
|
- month: '*'
|
||||||
- name: 'PATH=$PATH:/usr/sbin salt-call state.highstate'
|
- dayweek: '*'
|
||||||
- identifier: post_setup_cron
|
|
||||||
|
# Lock permissions on the backup directory
|
||||||
{% if GLOBALS.role not in ['eval', 'manager', 'managersearch', 'standalone'] %}
|
backupdir:
|
||||||
|
file.directory:
|
||||||
|
- name: /nsm/backup
|
||||||
|
- user: 0
|
||||||
|
- group: 0
|
||||||
|
- makedirs: True
|
||||||
|
- mode: 700
|
||||||
|
|
||||||
|
# Add config backup
|
||||||
|
/usr/sbin/so-config-backup > /dev/null 2>&1:
|
||||||
|
cron.present:
|
||||||
|
- user: root
|
||||||
|
- minute: '1'
|
||||||
|
- hour: '0'
|
||||||
|
- daymonth: '*'
|
||||||
|
- month: '*'
|
||||||
|
- dayweek: '*'
|
||||||
|
{% else %}
|
||||||
soversionfile:
|
soversionfile:
|
||||||
file.managed:
|
file.managed:
|
||||||
- name: /etc/soversion
|
- name: /etc/soversion
|
||||||
@@ -203,8 +339,34 @@ soversionfile:
|
|||||||
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% if GLOBALS.so_model and GLOBALS.so_model not in ['SO2AMI01', 'SO2AZI01', 'SO2GCI01'] %}
|
# Manager daemon.json
|
||||||
{% if GLOBALS.os == 'OEL' %}
|
docker_daemon:
|
||||||
|
file.managed:
|
||||||
|
- source: salt://common/files/daemon.json
|
||||||
|
- name: /etc/docker/daemon.json
|
||||||
|
- template: jinja
|
||||||
|
|
||||||
|
# Make sure Docker is always running
|
||||||
|
docker:
|
||||||
|
service.running:
|
||||||
|
- enable: True
|
||||||
|
- watch:
|
||||||
|
- file: docker_daemon
|
||||||
|
|
||||||
|
# Reserve OS ports for Docker proxy in case boot settings are not already applied/present
|
||||||
|
# 55000 = Wazuh, 57314 = Strelka, 47760-47860 = Zeek
|
||||||
|
dockerapplyports:
|
||||||
|
cmd.run:
|
||||||
|
- name: if [ ! -s /etc/sysctl.d/99-reserved-ports.conf ]; then sysctl -w net.ipv4.ip_local_reserved_ports="55000,57314,47760-47860"; fi
|
||||||
|
|
||||||
|
# Reserve OS ports for Docker proxy
|
||||||
|
dockerreserveports:
|
||||||
|
file.managed:
|
||||||
|
- source: salt://common/files/99-reserved-ports.conf
|
||||||
|
- name: /etc/sysctl.d/99-reserved-ports.conf
|
||||||
|
|
||||||
|
{% if salt['grains.get']('sosmodel', '') %}
|
||||||
|
{% if grains['os'] == 'CentOS' %}
|
||||||
# Install Raid tools
|
# Install Raid tools
|
||||||
raidpkgs:
|
raidpkgs:
|
||||||
pkg.installed:
|
pkg.installed:
|
||||||
@@ -215,10 +377,8 @@ raidpkgs:
|
|||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
# Install raid check cron
|
# Install raid check cron
|
||||||
so-raid-status:
|
/usr/sbin/so-raid-status > /dev/null 2>&1:
|
||||||
cron.present:
|
cron.present:
|
||||||
- name: '/usr/sbin/so-raid-status > /dev/null 2>&1'
|
|
||||||
- identifier: so-raid-status
|
|
||||||
- user: root
|
- user: root
|
||||||
- minute: '*/15'
|
- minute: '*/15'
|
||||||
- hour: '*'
|
- hour: '*'
|
||||||
@@ -226,7 +386,8 @@ so-raid-status:
|
|||||||
- month: '*'
|
- month: '*'
|
||||||
- dayweek: '*'
|
- dayweek: '*'
|
||||||
|
|
||||||
{% endif %}
|
{% endif %}
|
||||||
|
|
||||||
{% else %}
|
{% else %}
|
||||||
|
|
||||||
{{sls}}_state_not_allowed:
|
{{sls}}_state_not_allowed:
|
||||||
|
|||||||
@@ -1,86 +0,0 @@
|
|||||||
{% from 'vars/globals.map.jinja' import GLOBALS %}
|
|
||||||
|
|
||||||
{% if GLOBALS.os_family == 'Debian' %}
|
|
||||||
commonpkgs:
|
|
||||||
pkg.installed:
|
|
||||||
- skip_suggestions: True
|
|
||||||
- pkgs:
|
|
||||||
- apache2-utils
|
|
||||||
- wget
|
|
||||||
- ntpdate
|
|
||||||
- jq
|
|
||||||
- curl
|
|
||||||
- ca-certificates
|
|
||||||
- software-properties-common
|
|
||||||
- apt-transport-https
|
|
||||||
- openssl
|
|
||||||
- netcat-openbsd
|
|
||||||
- sqlite3
|
|
||||||
- libssl-dev
|
|
||||||
- procps
|
|
||||||
- python3-dateutil
|
|
||||||
- python3-docker
|
|
||||||
- python3-packaging
|
|
||||||
- python3-lxml
|
|
||||||
- git
|
|
||||||
- rsync
|
|
||||||
- vim
|
|
||||||
- tar
|
|
||||||
- unzip
|
|
||||||
{% if grains.oscodename != 'focal' %}
|
|
||||||
- python3-rich
|
|
||||||
{% endif %}
|
|
||||||
|
|
||||||
{% if grains.oscodename == 'focal' %}
|
|
||||||
# since Ubuntu requires and internet connection we can use pip to install modules
|
|
||||||
python3-pip:
|
|
||||||
pkg.installed
|
|
||||||
|
|
||||||
python-rich:
|
|
||||||
pip.installed:
|
|
||||||
- name: rich
|
|
||||||
- target: /usr/local/lib/python3.8/dist-packages/
|
|
||||||
- require:
|
|
||||||
- pkg: python3-pip
|
|
||||||
{% endif %}
|
|
||||||
{% endif %}
|
|
||||||
|
|
||||||
{% if GLOBALS.os_family == 'RedHat' %}
|
|
||||||
|
|
||||||
remove_mariadb:
|
|
||||||
pkg.removed:
|
|
||||||
- name: mariadb-devel
|
|
||||||
|
|
||||||
commonpkgs:
|
|
||||||
pkg.installed:
|
|
||||||
- skip_suggestions: True
|
|
||||||
- pkgs:
|
|
||||||
- python3-dnf-plugin-versionlock
|
|
||||||
- curl
|
|
||||||
- device-mapper-persistent-data
|
|
||||||
- fuse
|
|
||||||
- fuse-libs
|
|
||||||
- fuse-overlayfs
|
|
||||||
- fuse-common
|
|
||||||
- fuse3
|
|
||||||
- fuse3-libs
|
|
||||||
- git
|
|
||||||
- httpd-tools
|
|
||||||
- jq
|
|
||||||
- lvm2
|
|
||||||
- net-tools
|
|
||||||
- nmap-ncat
|
|
||||||
- procps-ng
|
|
||||||
- python3-docker
|
|
||||||
- python3-m2crypto
|
|
||||||
- python3-packaging
|
|
||||||
- python3-pyyaml
|
|
||||||
- python3-rich
|
|
||||||
- rsync
|
|
||||||
- sqlite
|
|
||||||
- tcpdump
|
|
||||||
- unzip
|
|
||||||
- wget
|
|
||||||
- yum-utils
|
|
||||||
|
|
||||||
{% endif %}
|
|
||||||
@@ -8,16 +8,6 @@ soup_scripts:
|
|||||||
- source: salt://common/tools/sbin
|
- source: salt://common/tools/sbin
|
||||||
- include_pat:
|
- include_pat:
|
||||||
- so-common
|
- so-common
|
||||||
- so-image-common
|
|
||||||
|
|
||||||
soup_manager_scripts:
|
|
||||||
file.recurse:
|
|
||||||
- name: /usr/sbin
|
|
||||||
- user: root
|
|
||||||
- group: root
|
|
||||||
- file_mode: 755
|
|
||||||
- source: salt://manager/tools/sbin
|
|
||||||
- include_pat:
|
|
||||||
- so-firewall
|
- so-firewall
|
||||||
- so-repo-sync
|
- so-image-common
|
||||||
- soup
|
- soup
|
||||||
|
|||||||
207
salt/common/tools/sbin/so-allow
Executable file
@@ -0,0 +1,207 @@
|
|||||||
|
#!/usr/bin/env python3
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
import ipaddress
|
||||||
|
import textwrap
|
||||||
|
import os
|
||||||
|
import subprocess
|
||||||
|
import sys
|
||||||
|
import argparse
|
||||||
|
import re
|
||||||
|
from lxml import etree as ET
|
||||||
|
from datetime import datetime as dt
|
||||||
|
from datetime import timezone as tz
|
||||||
|
|
||||||
|
|
||||||
|
LOCAL_SALT_DIR='/opt/so/saltstack/local'
|
||||||
|
WAZUH_CONF='/nsm/wazuh/etc/ossec.conf'
|
||||||
|
VALID_ROLES = {
|
||||||
|
'a': { 'role': 'analyst','desc': 'Analyst - 80/tcp, 443/tcp' },
|
||||||
|
'b': { 'role': 'beats_endpoint', 'desc': 'Logstash Beat - 5044/tcp' },
|
||||||
|
'e': { 'role': 'elasticsearch_rest', 'desc': 'Elasticsearch REST API - 9200/tcp' },
|
||||||
|
'f': { 'role': 'strelka_frontend', 'desc': 'Strelka frontend - 57314/tcp' },
|
||||||
|
'o': { 'role': 'osquery_endpoint', 'desc': 'Osquery endpoint - 8090/tcp' },
|
||||||
|
's': { 'role': 'syslog', 'desc': 'Syslog device - 514/tcp/udp' },
|
||||||
|
'w': { 'role': 'wazuh_agent', 'desc': 'Wazuh agent - 1514/tcp/udp' },
|
||||||
|
'p': { 'role': 'wazuh_api', 'desc': 'Wazuh API - 55000/tcp' },
|
||||||
|
'r': { 'role': 'wazuh_authd', 'desc': 'Wazuh registration service - 1515/tcp' }
|
||||||
|
}
|
||||||
|
|
||||||
|
|
||||||
|
def validate_ip_cidr(ip_cidr: str) -> bool:
|
||||||
|
try:
|
||||||
|
ipaddress.ip_address(ip_cidr)
|
||||||
|
except ValueError:
|
||||||
|
try:
|
||||||
|
ipaddress.ip_network(ip_cidr)
|
||||||
|
except ValueError:
|
||||||
|
return False
|
||||||
|
return True
|
||||||
|
|
||||||
|
|
||||||
|
def role_prompt() -> str:
|
||||||
|
print()
|
||||||
|
print('Choose the role for the IP or Range you would like to allow')
|
||||||
|
print()
|
||||||
|
for role in VALID_ROLES:
|
||||||
|
print(f'[{role}] - {VALID_ROLES[role]["desc"]}')
|
||||||
|
print()
|
||||||
|
role = input('Please enter your selection: ')
|
||||||
|
if role in VALID_ROLES.keys():
|
||||||
|
return VALID_ROLES[role]['role']
|
||||||
|
else:
|
||||||
|
print(f'Invalid role \'{role}\', please try again.', file=sys.stderr)
|
||||||
|
sys.exit(1)
|
||||||
|
|
||||||
|
|
||||||
|
def ip_prompt() -> str:
|
||||||
|
ip = input('Enter a single ip address or range to allow (ex: 10.10.10.10 or 10.10.0.0/16): ')
|
||||||
|
if validate_ip_cidr(ip):
|
||||||
|
return ip
|
||||||
|
else:
|
||||||
|
print(f'Invalid IP address or CIDR block \'{ip}\', please try again.', file=sys.stderr)
|
||||||
|
sys.exit(1)
|
||||||
|
|
||||||
|
|
||||||
|
def wazuh_enabled() -> bool:
|
||||||
|
file = f'{LOCAL_SALT_DIR}/pillar/global.sls'
|
||||||
|
with open(file, 'r') as pillar:
|
||||||
|
if 'wazuh: 1' in pillar.read():
|
||||||
|
return True
|
||||||
|
return False
|
||||||
|
|
||||||
|
|
||||||
|
def root_to_str(root: ET.ElementTree) -> str:
|
||||||
|
return ET.tostring(root, encoding='unicode', method='xml', xml_declaration=False, pretty_print=True)
|
||||||
|
|
||||||
|
|
||||||
|
def add_wl(ip):
|
||||||
|
parser = ET.XMLParser(remove_blank_text=True)
|
||||||
|
with open(WAZUH_CONF, 'rb') as wazuh_conf:
|
||||||
|
tree = ET.parse(wazuh_conf, parser)
|
||||||
|
root = tree.getroot()
|
||||||
|
|
||||||
|
source_comment = ET.Comment(f'Address {ip} added by /usr/sbin/so-allow on {dt.utcnow().replace(tzinfo=tz.utc).strftime("%a %b %e %H:%M:%S %Z %Y")}')
|
||||||
|
new_global = ET.Element("global")
|
||||||
|
new_wl = ET.SubElement(new_global, 'white_list')
|
||||||
|
new_wl.text = ip
|
||||||
|
|
||||||
|
root.append(source_comment)
|
||||||
|
root.append(new_global)
|
||||||
|
|
||||||
|
with open(WAZUH_CONF, 'w') as add_out:
|
||||||
|
add_out.write(root_to_str(root))
|
||||||
|
|
||||||
|
|
||||||
|
def apply(role: str, ip: str) -> int:
|
||||||
|
firewall_cmd = ['so-firewall', 'includehost', role, ip]
|
||||||
|
salt_cmd = ['salt-call', 'state.apply', '-l', 'quiet', 'firewall', 'queue=True']
|
||||||
|
restart_wazuh_cmd = ['so-wazuh-restart']
|
||||||
|
print(f'Adding {ip} to the {role} role. This can take a few seconds...')
|
||||||
|
cmd = subprocess.run(firewall_cmd)
|
||||||
|
if cmd.returncode == 0:
|
||||||
|
cmd = subprocess.run(salt_cmd, stdout=subprocess.DEVNULL)
|
||||||
|
else:
|
||||||
|
return cmd.returncode
|
||||||
|
if cmd.returncode == 0:
|
||||||
|
if wazuh_enabled() and role=='analyst':
|
||||||
|
try:
|
||||||
|
add_wl(ip)
|
||||||
|
print(f'Added whitelist entry for {ip} from {WAZUH_CONF}', file=sys.stderr)
|
||||||
|
except Exception as e:
|
||||||
|
print(f'Failed to add whitelist entry for {ip} from {WAZUH_CONF}', file=sys.stderr)
|
||||||
|
print(e)
|
||||||
|
return 1
|
||||||
|
print('Restarting OSSEC Server...')
|
||||||
|
cmd = subprocess.run(restart_wazuh_cmd)
|
||||||
|
else:
|
||||||
|
return cmd.returncode
|
||||||
|
else:
|
||||||
|
print(f'Commmand \'{" ".join(salt_cmd)}\' failed.', file=sys.stderr)
|
||||||
|
return cmd.returncode
|
||||||
|
if cmd.returncode != 0:
|
||||||
|
print('Failed to restart OSSEC server.')
|
||||||
|
return cmd.returncode
|
||||||
|
|
||||||
|
|
||||||
|
def main():
|
||||||
|
if os.geteuid() != 0:
|
||||||
|
print('You must run this script as root', file=sys.stderr)
|
||||||
|
sys.exit(1)
|
||||||
|
|
||||||
|
main_parser = argparse.ArgumentParser(
|
||||||
|
formatter_class=argparse.RawDescriptionHelpFormatter,
|
||||||
|
epilog=textwrap.dedent(f'''\
|
||||||
|
additional information:
|
||||||
|
To use this script in interactive mode call it with no arguments
|
||||||
|
'''
|
||||||
|
))
|
||||||
|
|
||||||
|
group = main_parser.add_argument_group(title='roles')
|
||||||
|
group.add_argument('-a', dest='roles', action='append_const', const=VALID_ROLES['a']['role'], help="Analyst - 80/tcp, 443/tcp")
|
||||||
|
group.add_argument('-b', dest='roles', action='append_const', const=VALID_ROLES['b']['role'], help="Logstash Beat - 5044/tcp")
|
||||||
|
group.add_argument('-e', dest='roles', action='append_const', const=VALID_ROLES['e']['role'], help="Elasticsearch REST API - 9200/tcp")
|
||||||
|
group.add_argument('-f', dest='roles', action='append_const', const=VALID_ROLES['f']['role'], help="Strelka frontend - 57314/tcp")
|
||||||
|
group.add_argument('-o', dest='roles', action='append_const', const=VALID_ROLES['o']['role'], help="Osquery endpoint - 8090/tcp")
|
||||||
|
group.add_argument('-s', dest='roles', action='append_const', const=VALID_ROLES['s']['role'], help="Syslog device - 514/tcp/udp")
|
||||||
|
group.add_argument('-w', dest='roles', action='append_const', const=VALID_ROLES['w']['role'], help="Wazuh agent - 1514/tcp/udp")
|
||||||
|
group.add_argument('-p', dest='roles', action='append_const', const=VALID_ROLES['p']['role'], help="Wazuh API - 55000/tcp")
|
||||||
|
group.add_argument('-r', dest='roles', action='append_const', const=VALID_ROLES['r']['role'], help="Wazuh registration service - 1515/tcp")
|
||||||
|
|
||||||
|
ip_g = main_parser.add_argument_group(title='allow')
|
||||||
|
ip_g.add_argument('-i', help="IP or CIDR block to disallow connections from, requires at least one role argument", metavar='', dest='ip')
|
||||||
|
|
||||||
|
args = main_parser.parse_args(sys.argv[1:])
|
||||||
|
|
||||||
|
if args.roles is None:
|
||||||
|
role = role_prompt()
|
||||||
|
ip = ip_prompt()
|
||||||
|
try:
|
||||||
|
return_code = apply(role, ip)
|
||||||
|
except Exception as e:
|
||||||
|
print(f'Unexpected exception occurred: {e}', file=sys.stderr)
|
||||||
|
return_code = e.errno
|
||||||
|
sys.exit(return_code)
|
||||||
|
elif args.roles is not None and args.ip is None:
|
||||||
|
if os.environ.get('IP') is None:
|
||||||
|
main_parser.print_help()
|
||||||
|
sys.exit(1)
|
||||||
|
else:
|
||||||
|
args.ip = os.environ['IP']
|
||||||
|
|
||||||
|
if validate_ip_cidr(args.ip):
|
||||||
|
try:
|
||||||
|
for role in args.roles:
|
||||||
|
return_code = apply(role, args.ip)
|
||||||
|
if return_code > 0:
|
||||||
|
break
|
||||||
|
except Exception as e:
|
||||||
|
print(f'Unexpected exception occurred: {e}', file=sys.stderr)
|
||||||
|
return_code = e.errno
|
||||||
|
else:
|
||||||
|
print(f'Invalid IP address or CIDR block \'{args.ip}\', please try again.', file=sys.stderr)
|
||||||
|
return_code = 1
|
||||||
|
|
||||||
|
sys.exit(return_code)
|
||||||
|
|
||||||
|
|
||||||
|
if __name__ == '__main__':
|
||||||
|
try:
|
||||||
|
main()
|
||||||
|
except KeyboardInterrupt:
|
||||||
|
sys.exit(1)
|
||||||
|
|
||||||
23
salt/common/tools/sbin/so-allow-view
Executable file
@@ -0,0 +1,23 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
echo ""
|
||||||
|
echo "Hosts/Networks that have access to login to the Security Onion Console:"
|
||||||
|
|
||||||
|
so-firewall includedhosts analyst
|
||||||
100
salt/common/tools/sbin/so-analyst-install
Executable file
@@ -0,0 +1,100 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
doc_workstation_url="https://docs.securityonion.net/en/2.3/analyst-vm.html"
|
||||||
|
{# we only want the script to install the workstation if it is CentOS -#}
|
||||||
|
{% if grains.os == 'CentOS' -%}
|
||||||
|
{# if this is a manager -#}
|
||||||
|
{% if grains.master == grains.id.split('_')|first -%}
|
||||||
|
|
||||||
|
source /usr/sbin/so-common
|
||||||
|
pillar_file="/opt/so/saltstack/local/pillar/minions/{{grains.id}}.sls"
|
||||||
|
|
||||||
|
if [ -f "$pillar_file" ]; then
|
||||||
|
if ! grep -q "^workstation:$" "$pillar_file"; then
|
||||||
|
|
||||||
|
FIRSTPASS=yes
|
||||||
|
while [[ $INSTALL != "yes" ]] && [[ $INSTALL != "no" ]]; do
|
||||||
|
if [[ "$FIRSTPASS" == "yes" ]]; then
|
||||||
|
echo "###########################################"
|
||||||
|
echo "## ** W A R N I N G ** ##"
|
||||||
|
echo "## _______________________________ ##"
|
||||||
|
echo "## ##"
|
||||||
|
echo "## Installing the Security Onion ##"
|
||||||
|
echo "## analyst node on this device will ##"
|
||||||
|
echo "## make permanent changes to ##"
|
||||||
|
echo "## the system. ##"
|
||||||
|
echo "## A system reboot will be required ##"
|
||||||
|
echo "## to complete the install. ##"
|
||||||
|
echo "## ##"
|
||||||
|
echo "###########################################"
|
||||||
|
echo "Do you wish to continue? (Type the entire word 'yes' to proceed or 'no' to exit)"
|
||||||
|
FIRSTPASS=no
|
||||||
|
else
|
||||||
|
echo "Please type 'yes' to continue or 'no' to exit."
|
||||||
|
fi
|
||||||
|
read INSTALL
|
||||||
|
done
|
||||||
|
|
||||||
|
if [[ $INSTALL == "no" ]]; then
|
||||||
|
echo "Exiting analyst node installation."
|
||||||
|
exit 0
|
||||||
|
fi
|
||||||
|
|
||||||
|
# Add workstation pillar to the minion's pillar file
|
||||||
|
printf '%s\n'\
|
||||||
|
"workstation:"\
|
||||||
|
" gui:"\
|
||||||
|
" enabled: true"\
|
||||||
|
"" >> "$pillar_file"
|
||||||
|
echo "Applying the workstation state. This could take some time since there are many packages that need to be installed."
|
||||||
|
if salt-call state.apply workstation -linfo queue=True; then # make sure the state ran successfully
|
||||||
|
echo ""
|
||||||
|
echo "Analyst workstation has been installed!"
|
||||||
|
echo "Press ENTER to reboot or Ctrl-C to cancel."
|
||||||
|
read pause
|
||||||
|
|
||||||
|
reboot;
|
||||||
|
else
|
||||||
|
echo "There was an issue applying the workstation state. Please review the log above or at /opt/so/logs/salt/minion."
|
||||||
|
fi
|
||||||
|
else # workstation is already added
|
||||||
|
echo "The workstation pillar already exists in $pillar_file."
|
||||||
|
echo "To enable/disable the gui, set 'workstation:gui:enabled' to true or false in $pillar_file."
|
||||||
|
echo "Additional documentation can be found at $doc_workstation_url."
|
||||||
|
fi
|
||||||
|
else # if the pillar file doesn't exist
|
||||||
|
echo "Could not find $pillar_file and add the workstation pillar."
|
||||||
|
fi
|
||||||
|
|
||||||
|
{#- if this is not a manager #}
|
||||||
|
{% else -%}
|
||||||
|
|
||||||
|
echo "Since this is not a manager, the pillar values to enable analyst workstation must be set manually. Please view the documentation at $doc_workstation_url."
|
||||||
|
|
||||||
|
{#- endif if this is a manager #}
|
||||||
|
{% endif -%}
|
||||||
|
|
||||||
|
{#- if not CentOS #}
|
||||||
|
{%- else %}
|
||||||
|
|
||||||
|
echo "The Analyst Workstation can only be installed on CentOS. Please view the documentation at $doc_workstation_url."
|
||||||
|
|
||||||
|
{#- endif grains.os == CentOS #}
|
||||||
|
{% endif -%}
|
||||||
|
|
||||||
|
exit 0
|
||||||
@@ -1,11 +1,19 @@
|
|||||||
#!/bin/bash
|
#!/bin/bash
|
||||||
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
#
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
# This program is free software: you can redistribute it and/or modify
|
||||||
# Elastic License 2.0.
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
. /usr/sbin/so-common
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
|||||||
@@ -1,34 +1,26 @@
|
|||||||
#!/bin/bash
|
#!/bin/bash
|
||||||
#
|
#
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
#
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
# This program is free software: you can redistribute it and/or modify
|
||||||
# Elastic License 2.0.
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
# Elastic agent is not managed by salt. Because of this we must store this base information in a
|
# (at your option) any later version.
|
||||||
# script that accompanies the soup system. Since so-common is one of those special soup files,
|
#
|
||||||
# and since this same logic is required during installation, it's included in this file.
|
# This program is distributed in the hope that it will be useful,
|
||||||
ELASTIC_AGENT_TARBALL_VERSION="8.10.4"
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
ELASTIC_AGENT_URL="https://repo.securityonion.net/file/so-repo/prod/2.4/elasticagent/elastic-agent_SO-$ELASTIC_AGENT_TARBALL_VERSION.tar.gz"
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
ELASTIC_AGENT_MD5_URL="https://repo.securityonion.net/file/so-repo/prod/2.4/elasticagent/elastic-agent_SO-$ELASTIC_AGENT_TARBALL_VERSION.md5"
|
# GNU General Public License for more details.
|
||||||
ELASTIC_AGENT_FILE="/nsm/elastic-fleet/artifacts/elastic-agent_SO-$ELASTIC_AGENT_TARBALL_VERSION.tar.gz"
|
#
|
||||||
ELASTIC_AGENT_MD5="/nsm/elastic-fleet/artifacts/elastic-agent_SO-$ELASTIC_AGENT_TARBALL_VERSION.md5"
|
# You should have received a copy of the GNU General Public License
|
||||||
ELASTIC_AGENT_EXPANSION_DIR=/nsm/elastic-fleet/artifacts/beats/elastic-agent
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
DEFAULT_SALT_DIR=/opt/so/saltstack/default
|
DEFAULT_SALT_DIR=/opt/so/saltstack/default
|
||||||
DOC_BASE_URL="https://docs.securityonion.net/en/2.4"
|
|
||||||
|
|
||||||
if [ -z $NOROOT ]; then
|
# Check for prerequisites
|
||||||
# Check for prerequisites
|
if [ "$(id -u)" -ne 0 ]; then
|
||||||
if [ "$(id -u)" -ne 0 ]; then
|
echo "This script must be run using sudo!"
|
||||||
echo "This script must be run using sudo!"
|
exit 1
|
||||||
exit 1
|
|
||||||
fi
|
|
||||||
fi
|
|
||||||
|
|
||||||
# Ensure /usr/sbin is in path
|
|
||||||
if ! echo "$PATH" | grep -q "/usr/sbin"; then
|
|
||||||
export PATH="$PATH:/usr/sbin"
|
|
||||||
fi
|
fi
|
||||||
|
|
||||||
# Define a banner to separate sections
|
# Define a banner to separate sections
|
||||||
@@ -64,37 +56,33 @@ add_interface_bond0() {
|
|||||||
ethtool -K "$BNIC" $i off &>/dev/null
|
ethtool -K "$BNIC" $i off &>/dev/null
|
||||||
fi
|
fi
|
||||||
done
|
done
|
||||||
|
# Check if the bond slave connection has already been created
|
||||||
|
nmcli -f name,uuid -p con | grep -q "bond0-slave-$BNIC"
|
||||||
|
local found_int=$?
|
||||||
|
|
||||||
if ! [[ $is_cloud ]]; then
|
if [[ $found_int != 0 ]]; then
|
||||||
# Check if the bond slave connection has already been created
|
# Create the slave interface and assign it to the bond
|
||||||
nmcli -f name,uuid -p con | grep -q "bond0-slave-$BNIC"
|
nmcli con add type ethernet ifname "$BNIC" con-name "bond0-slave-$BNIC" master bond0 -- \
|
||||||
local found_int=$?
|
ethernet.mtu "$MTU" \
|
||||||
|
connection.autoconnect "yes"
|
||||||
|
else
|
||||||
|
local int_uuid
|
||||||
|
int_uuid=$(nmcli -f name,uuid -p con | sed -n "s/bond0-slave-$BNIC //p" | tr -d ' ')
|
||||||
|
|
||||||
if [[ $found_int != 0 ]]; then
|
nmcli con mod "$int_uuid" \
|
||||||
# Create the slave interface and assign it to the bond
|
ethernet.mtu "$MTU" \
|
||||||
nmcli con add type ethernet ifname "$BNIC" con-name "bond0-slave-$BNIC" master bond0 -- \
|
connection.autoconnect "yes"
|
||||||
ethernet.mtu "$MTU" \
|
fi
|
||||||
connection.autoconnect "yes"
|
|
||||||
else
|
|
||||||
local int_uuid
|
|
||||||
int_uuid=$(nmcli -f name,uuid -p con | sed -n "s/bond0-slave-$BNIC //p" | tr -d ' ')
|
|
||||||
|
|
||||||
nmcli con mod "$int_uuid" \
|
|
||||||
ethernet.mtu "$MTU" \
|
|
||||||
connection.autoconnect "yes"
|
|
||||||
fi
|
|
||||||
fi
|
|
||||||
|
|
||||||
ip link set dev "$BNIC" arp off multicast off allmulticast off promisc on
|
ip link set dev "$BNIC" arp off multicast off allmulticast off promisc on
|
||||||
|
|
||||||
if ! [[ $is_cloud ]]; then
|
# Bring the slave interface up
|
||||||
# Bring the slave interface up
|
if [[ $verbose == true ]]; then
|
||||||
if [[ $verbose == true ]]; then
|
nmcli con up "bond0-slave-$BNIC"
|
||||||
nmcli con up "bond0-slave-$BNIC"
|
else
|
||||||
else
|
nmcli con up "bond0-slave-$BNIC" &>/dev/null
|
||||||
nmcli con up "bond0-slave-$BNIC" &>/dev/null
|
|
||||||
fi
|
|
||||||
fi
|
fi
|
||||||
|
|
||||||
if [ "$nic_error" != 0 ]; then
|
if [ "$nic_error" != 0 ]; then
|
||||||
return "$nic_error"
|
return "$nic_error"
|
||||||
fi
|
fi
|
||||||
@@ -133,47 +121,34 @@ check_elastic_license() {
|
|||||||
}
|
}
|
||||||
|
|
||||||
check_salt_master_status() {
|
check_salt_master_status() {
|
||||||
local count=0
|
local timeout=$1
|
||||||
local attempts="${1:- 10}"
|
echo "Checking if we can talk to the salt master"
|
||||||
current_time="$(date '+%b %d %H:%M:%S')"
|
salt-call state.show_top concurrent=true
|
||||||
echo "Checking if we can access the salt master and that it is ready at: ${current_time}"
|
|
||||||
while ! salt-call state.show_top -l error concurrent=true 1> /dev/null; do
|
return
|
||||||
current_time="$(date '+%b %d %H:%M:%S')"
|
|
||||||
echo "Can't access salt master or it is not ready at: ${current_time}"
|
|
||||||
((count+=1))
|
|
||||||
if [[ $count -eq $attempts ]]; then
|
|
||||||
# 10 attempts takes about 5.5 minutes
|
|
||||||
echo "Gave up trying to access salt-master"
|
|
||||||
return 1
|
|
||||||
fi
|
|
||||||
done
|
|
||||||
current_time="$(date '+%b %d %H:%M:%S')"
|
|
||||||
echo "Successfully accessed and salt master ready at: ${current_time}"
|
|
||||||
return 0
|
|
||||||
}
|
}
|
||||||
|
|
||||||
# this is only intended to be used to check the status of the minion from a salt master
|
|
||||||
check_salt_minion_status() {
|
check_salt_minion_status() {
|
||||||
local minion="$1"
|
local timeout=$1
|
||||||
local timeout="${2:-5}"
|
echo "Checking if the salt minion will respond to jobs" >> "$setup_log" 2>&1
|
||||||
local logfile="${3:-'/dev/stdout'}"
|
salt "$MINION_ID" test.ping -t $timeout > /dev/null 2>&1
|
||||||
echo "Checking if the salt minion: $minion will respond to jobs" >> "$logfile" 2>&1
|
|
||||||
salt "$minion" test.ping -t $timeout > /dev/null 2>&1
|
|
||||||
local status=$?
|
local status=$?
|
||||||
if [ $status -gt 0 ]; then
|
if [ $status -gt 0 ]; then
|
||||||
echo " Minion did not respond" >> "$logfile" 2>&1
|
echo " Minion did not respond" >> "$setup_log" 2>&1
|
||||||
else
|
else
|
||||||
echo " Received job response from salt minion" >> "$logfile" 2>&1
|
echo " Received job response from salt minion" >> "$setup_log" 2>&1
|
||||||
fi
|
fi
|
||||||
|
|
||||||
return $status
|
return $status
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
copy_new_files() {
|
copy_new_files() {
|
||||||
# Copy new files over to the salt dir
|
# Copy new files over to the salt dir
|
||||||
cd $UPDATE_DIR
|
cd $UPDATE_DIR
|
||||||
rsync -a salt $DEFAULT_SALT_DIR/ --delete
|
rsync -a salt $DEFAULT_SALT_DIR/
|
||||||
rsync -a pillar $DEFAULT_SALT_DIR/ --delete
|
rsync -a pillar $DEFAULT_SALT_DIR/
|
||||||
chown -R socore:socore $DEFAULT_SALT_DIR/
|
chown -R socore:socore $DEFAULT_SALT_DIR/
|
||||||
chmod 755 $DEFAULT_SALT_DIR/pillar/firewall/addfirewall.sh
|
chmod 755 $DEFAULT_SALT_DIR/pillar/firewall/addfirewall.sh
|
||||||
cd /tmp
|
cd /tmp
|
||||||
@@ -183,44 +158,19 @@ disable_fastestmirror() {
|
|||||||
sed -i 's/enabled=1/enabled=0/' /etc/yum/pluginconf.d/fastestmirror.conf
|
sed -i 's/enabled=1/enabled=0/' /etc/yum/pluginconf.d/fastestmirror.conf
|
||||||
}
|
}
|
||||||
|
|
||||||
download_and_verify() {
|
|
||||||
source_url=$1
|
|
||||||
source_md5_url=$2
|
|
||||||
dest_file=$3
|
|
||||||
md5_file=$4
|
|
||||||
expand_dir=$5
|
|
||||||
|
|
||||||
if [[ -n "$expand_dir" ]]; then
|
|
||||||
mkdir -p "$expand_dir"
|
|
||||||
fi
|
|
||||||
|
|
||||||
if ! verify_md5_checksum "$dest_file" "$md5_file"; then
|
|
||||||
retry 15 10 "curl --fail --retry 5 --retry-delay 15 -L '$source_url' --output '$dest_file'" "" ""
|
|
||||||
retry 15 10 "curl --fail --retry 5 --retry-delay 15 -L '$source_md5_url' --output '$md5_file'" "" ""
|
|
||||||
|
|
||||||
if verify_md5_checksum "$dest_file" "$md5_file"; then
|
|
||||||
echo "Source file and checksum are good."
|
|
||||||
else
|
|
||||||
echo "Unable to download and verify the source file and checksum."
|
|
||||||
return 1
|
|
||||||
fi
|
|
||||||
fi
|
|
||||||
|
|
||||||
if [[ -n "$expand_dir" ]]; then
|
|
||||||
tar -xf "$dest_file" -C "$expand_dir"
|
|
||||||
fi
|
|
||||||
}
|
|
||||||
|
|
||||||
elastic_license() {
|
elastic_license() {
|
||||||
|
|
||||||
read -r -d '' message <<- EOM
|
read -r -d '' message <<- EOM
|
||||||
\n
|
\n
|
||||||
Elastic Stack binaries and Security Onion components are only available under the Elastic License version 2 (ELv2):
|
Starting in Elastic Stack version 7.11, the Elastic Stack binaries are only available under the Elastic License:
|
||||||
https://securityonion.net/license/
|
https://securityonion.net/elastic-license
|
||||||
|
|
||||||
Do you agree to the terms of ELv2?
|
Please review the Elastic License:
|
||||||
|
https://www.elastic.co/licensing/elastic-license
|
||||||
|
|
||||||
If so, type AGREE to accept ELv2 and continue. Otherwise, press Enter to exit this program without making any changes.
|
Do you agree to the terms of the Elastic License?
|
||||||
|
|
||||||
|
If so, type AGREE to accept the Elastic License and continue. Otherwise, press Enter to exit this program without making any changes.
|
||||||
EOM
|
EOM
|
||||||
|
|
||||||
AGREED=$(whiptail --title "$whiptail_title" --inputbox \
|
AGREED=$(whiptail --title "$whiptail_title" --inputbox \
|
||||||
@@ -249,20 +199,19 @@ get_random_value() {
|
|||||||
}
|
}
|
||||||
|
|
||||||
gpg_rpm_import() {
|
gpg_rpm_import() {
|
||||||
if [[ $is_oracle ]]; then
|
if [[ "$OS" == "centos" ]]; then
|
||||||
if [[ "$WHATWOULDYOUSAYYAHDOHERE" == "setup" ]]; then
|
if [[ "$WHATWOULDYOUSAYYAHDOHERE" == "setup" ]]; then
|
||||||
local RPMKEYSLOC="../salt/repo/client/files/$OS/keys"
|
local RPMKEYSLOC="../salt/repo/client/files/centos/keys"
|
||||||
else
|
else
|
||||||
local RPMKEYSLOC="$UPDATE_DIR/salt/repo/client/files/$OS/keys"
|
local RPMKEYSLOC="$UPDATE_DIR/salt/repo/client/files/centos/keys"
|
||||||
fi
|
fi
|
||||||
RPMKEYS=('RPM-GPG-KEY-oracle' 'RPM-GPG-KEY-EPEL-9' 'SALT-PROJECT-GPG-PUBKEY-2023.pub' 'docker.pub' 'securityonion.pub')
|
|
||||||
for RPMKEY in "${RPMKEYS[@]}"; do
|
RPMKEYS=('RPM-GPG-KEY-EPEL-7' 'GPG-KEY-WAZUH' 'docker.pub' 'SALTSTACK-GPG-KEY.pub' 'securityonion.pub')
|
||||||
|
|
||||||
|
for RPMKEY in "${RPMKEYS[@]}"; do
|
||||||
rpm --import $RPMKEYSLOC/$RPMKEY
|
rpm --import $RPMKEYSLOC/$RPMKEY
|
||||||
echo "Imported $RPMKEY"
|
echo "Imported $RPMKEY"
|
||||||
done
|
done
|
||||||
elif [[ $is_rpm ]]; then
|
|
||||||
echo "Importing the security onion GPG key"
|
|
||||||
rpm --import ../salt/repo/client/files/oracle/keys/securityonion.pub
|
|
||||||
fi
|
fi
|
||||||
}
|
}
|
||||||
|
|
||||||
@@ -275,15 +224,12 @@ init_monitor() {
|
|||||||
|
|
||||||
if [[ $MONITORNIC == "bond0" ]]; then
|
if [[ $MONITORNIC == "bond0" ]]; then
|
||||||
BIFACES=$(lookup_bond_interfaces)
|
BIFACES=$(lookup_bond_interfaces)
|
||||||
for i in rx tx sg tso ufo gso gro lro rx-vlan-offload tx-vlan-offload generic-receive-offload generic-segmentation-offload tcp-segmentation-offload; do
|
|
||||||
ethtool -K "$MONITORNIC" "$i" off;
|
|
||||||
done
|
|
||||||
else
|
else
|
||||||
BIFACES=$MONITORNIC
|
BIFACES=$MONITORNIC
|
||||||
fi
|
fi
|
||||||
|
|
||||||
for DEVICE_IFACE in $BIFACES; do
|
for DEVICE_IFACE in $BIFACES; do
|
||||||
for i in rx tx sg tso ufo gso gro lro rx-vlan-offload tx-vlan-offload generic-receive-offload generic-segmentation-offload tcp-segmentation-offload; do
|
for i in rx tx sg tso ufo gso gro lro; do
|
||||||
ethtool -K "$DEVICE_IFACE" "$i" off;
|
ethtool -K "$DEVICE_IFACE" "$i" off;
|
||||||
done
|
done
|
||||||
ip link set dev "$DEVICE_IFACE" arp off multicast off allmulticast off promisc on
|
ip link set dev "$DEVICE_IFACE" arp off multicast off allmulticast off promisc on
|
||||||
@@ -291,17 +237,31 @@ init_monitor() {
|
|||||||
}
|
}
|
||||||
|
|
||||||
is_manager_node() {
|
is_manager_node() {
|
||||||
grep "role: so-" /etc/salt/grains | grep -E "manager|eval|managersearch|standalone|import" &> /dev/null
|
# Check to see if this is a manager node
|
||||||
|
role=$(lookup_role)
|
||||||
|
is_single_node_grid && return 0
|
||||||
|
[ $role == 'manager' ] && return 0
|
||||||
|
[ $role == 'managersearch' ] && return 0
|
||||||
|
[ $role == 'helix' ] && return 0
|
||||||
|
return 1
|
||||||
}
|
}
|
||||||
|
|
||||||
is_sensor_node() {
|
is_sensor_node() {
|
||||||
# Check to see if this is a sensor (forward) node
|
# Check to see if this is a sensor (forward) node
|
||||||
|
role=$(lookup_role)
|
||||||
is_single_node_grid && return 0
|
is_single_node_grid && return 0
|
||||||
grep "role: so-" /etc/salt/grains | grep -E "sensor|heavynode" &> /dev/null
|
[ $role == 'sensor' ] && return 0
|
||||||
|
[ $role == 'heavynode' ] && return 0
|
||||||
|
[ $role == 'helix' ] && return 0
|
||||||
|
return 1
|
||||||
}
|
}
|
||||||
|
|
||||||
is_single_node_grid() {
|
is_single_node_grid() {
|
||||||
grep "role: so-" /etc/salt/grains | grep -E "eval|standalone|import" &> /dev/null
|
role=$(lookup_role)
|
||||||
|
[ $role == 'eval' ] && return 0
|
||||||
|
[ $role == 'standalone' ] && return 0
|
||||||
|
[ $role == 'import' ] && return 0
|
||||||
|
return 1
|
||||||
}
|
}
|
||||||
|
|
||||||
lookup_bond_interfaces() {
|
lookup_bond_interfaces() {
|
||||||
@@ -355,17 +315,6 @@ lookup_role() {
|
|||||||
echo ${pieces[1]}
|
echo ${pieces[1]}
|
||||||
}
|
}
|
||||||
|
|
||||||
is_feature_enabled() {
|
|
||||||
feature=$1
|
|
||||||
enabled=$(lookup_salt_value features)
|
|
||||||
for cur in $enabled; do
|
|
||||||
if [[ "$feature" == "$cur" ]]; then
|
|
||||||
return 0
|
|
||||||
fi
|
|
||||||
done
|
|
||||||
return 1
|
|
||||||
}
|
|
||||||
|
|
||||||
require_manager() {
|
require_manager() {
|
||||||
if is_manager_node; then
|
if is_manager_node; then
|
||||||
echo "This is a manager, so we can proceed."
|
echo "This is a manager, so we can proceed."
|
||||||
@@ -397,10 +346,6 @@ retry() {
|
|||||||
echo "<Start of output>"
|
echo "<Start of output>"
|
||||||
echo "$output"
|
echo "$output"
|
||||||
echo "<End of output>"
|
echo "<End of output>"
|
||||||
if [[ $exitcode -eq 0 ]]; then
|
|
||||||
echo "Forcing exit code to 1"
|
|
||||||
exitcode=1
|
|
||||||
fi
|
|
||||||
fi
|
fi
|
||||||
elif [ -n "$failedOutput" ]; then
|
elif [ -n "$failedOutput" ]; then
|
||||||
if [[ "$output" =~ "$failedOutput" ]]; then
|
if [[ "$output" =~ "$failedOutput" ]]; then
|
||||||
@@ -409,7 +354,7 @@ retry() {
|
|||||||
echo "$output"
|
echo "$output"
|
||||||
echo "<End of output>"
|
echo "<End of output>"
|
||||||
if [[ $exitcode -eq 0 ]]; then
|
if [[ $exitcode -eq 0 ]]; then
|
||||||
echo "Forcing exit code to 1"
|
echo "The exitcode was 0, but we are setting to 1 since we found $failedOutput in the output."
|
||||||
exitcode=1
|
exitcode=1
|
||||||
fi
|
fi
|
||||||
else
|
else
|
||||||
@@ -447,82 +392,19 @@ run_check_net_err() {
|
|||||||
fi
|
fi
|
||||||
}
|
}
|
||||||
|
|
||||||
wait_for_salt_minion() {
|
set_cron_service_name() {
|
||||||
local minion="$1"
|
if [[ "$OS" == "centos" ]]; then
|
||||||
local timeout="${2:-5}"
|
cron_service_name="crond"
|
||||||
local logfile="${3:-'/dev/stdout'}"
|
else
|
||||||
retry 60 5 "journalctl -u salt-minion.service | grep 'Minion is ready to receive requests'" >> "$logfile" 2>&1 || fail
|
cron_service_name="cron"
|
||||||
local attempt=0
|
fi
|
||||||
# each attempts would take about 15 seconds
|
|
||||||
local maxAttempts=20
|
|
||||||
until check_salt_minion_status "$minion" "$timeout" "$logfile"; do
|
|
||||||
attempt=$((attempt+1))
|
|
||||||
if [[ $attempt -eq $maxAttempts ]]; then
|
|
||||||
return 1
|
|
||||||
fi
|
|
||||||
sleep 10
|
|
||||||
done
|
|
||||||
return 0
|
|
||||||
}
|
|
||||||
|
|
||||||
salt_minion_count() {
|
|
||||||
local MINIONDIR="/opt/so/saltstack/local/pillar/minions"
|
|
||||||
MINIONCOUNT=$(ls -la $MINIONDIR/*.sls | grep -v adv_ | wc -l)
|
|
||||||
|
|
||||||
}
|
}
|
||||||
|
|
||||||
set_os() {
|
set_os() {
|
||||||
if [ -f /etc/redhat-release ]; then
|
if [ -f /etc/redhat-release ]; then
|
||||||
if grep -q "Rocky Linux release 9" /etc/redhat-release; then
|
OS=centos
|
||||||
OS=rocky
|
else
|
||||||
OSVER=9
|
OS=ubuntu
|
||||||
is_rocky=true
|
|
||||||
is_rpm=true
|
|
||||||
elif grep -q "CentOS Stream release 9" /etc/redhat-release; then
|
|
||||||
OS=centos
|
|
||||||
OSVER=9
|
|
||||||
is_centos=true
|
|
||||||
is_rpm=true
|
|
||||||
elif grep -q "AlmaLinux release 9" /etc/redhat-release; then
|
|
||||||
OS=alma
|
|
||||||
OSVER=9
|
|
||||||
is_alma=true
|
|
||||||
is_rpm=true
|
|
||||||
elif grep -q "Red Hat Enterprise Linux release 9" /etc/redhat-release; then
|
|
||||||
if [ -f /etc/oracle-release ]; then
|
|
||||||
OS=oracle
|
|
||||||
OSVER=9
|
|
||||||
is_oracle=true
|
|
||||||
is_rpm=true
|
|
||||||
else
|
|
||||||
OS=rhel
|
|
||||||
OSVER=9
|
|
||||||
is_rhel=true
|
|
||||||
is_rpm=true
|
|
||||||
fi
|
|
||||||
fi
|
|
||||||
cron_service_name="crond"
|
|
||||||
elif [ -f /etc/os-release ]; then
|
|
||||||
if grep -q "UBUNTU_CODENAME=focal" /etc/os-release; then
|
|
||||||
OSVER=focal
|
|
||||||
UBVER=20.04
|
|
||||||
OS=ubuntu
|
|
||||||
is_ubuntu=true
|
|
||||||
is_deb=true
|
|
||||||
elif grep -q "UBUNTU_CODENAME=jammy" /etc/os-release; then
|
|
||||||
OSVER=jammy
|
|
||||||
UBVER=22.04
|
|
||||||
OS=ubuntu
|
|
||||||
is_ubuntu=true
|
|
||||||
is_deb=true
|
|
||||||
elif grep -q "VERSION_CODENAME=bookworm" /etc/os-release; then
|
|
||||||
OSVER=bookworm
|
|
||||||
DEBVER=12
|
|
||||||
is_debian=true
|
|
||||||
OS=debian
|
|
||||||
is_deb=true
|
|
||||||
fi
|
|
||||||
cron_service_name="cron"
|
|
||||||
fi
|
fi
|
||||||
}
|
}
|
||||||
|
|
||||||
@@ -531,7 +413,7 @@ set_minionid() {
|
|||||||
}
|
}
|
||||||
|
|
||||||
set_palette() {
|
set_palette() {
|
||||||
if [[ $is_deb ]]; then
|
if [ "$OS" == ubuntu ]; then
|
||||||
update-alternatives --set newt-palette /etc/newt/palette.original
|
update-alternatives --set newt-palette /etc/newt/palette.original
|
||||||
fi
|
fi
|
||||||
}
|
}
|
||||||
@@ -555,10 +437,6 @@ set_version() {
|
|||||||
fi
|
fi
|
||||||
}
|
}
|
||||||
|
|
||||||
status () {
|
|
||||||
printf "\n=========================================================================\n$(date) | $1\n=========================================================================\n"
|
|
||||||
}
|
|
||||||
|
|
||||||
systemctl_func() {
|
systemctl_func() {
|
||||||
local action=$1
|
local action=$1
|
||||||
local echo_action=$1
|
local echo_action=$1
|
||||||
@@ -582,11 +460,6 @@ has_uppercase() {
|
|||||||
|| return 1
|
|| return 1
|
||||||
}
|
}
|
||||||
|
|
||||||
update_elastic_agent() {
|
|
||||||
echo "Checking if Elastic Agent update is necessary..."
|
|
||||||
download_and_verify "$ELASTIC_AGENT_URL" "$ELASTIC_AGENT_MD5_URL" "$ELASTIC_AGENT_FILE" "$ELASTIC_AGENT_MD5" "$ELASTIC_AGENT_EXPANSION_DIR"
|
|
||||||
}
|
|
||||||
|
|
||||||
valid_cidr() {
|
valid_cidr() {
|
||||||
# Verify there is a backslash in the string
|
# Verify there is a backslash in the string
|
||||||
echo "$1" | grep -qP "^[^/]+/[^/]+$" || return 1
|
echo "$1" | grep -qP "^[^/]+/[^/]+$" || return 1
|
||||||
@@ -645,18 +518,6 @@ valid_hostname() {
|
|||||||
[[ $hostname =~ ^[a-zA-Z0-9\-]+$ ]] && [[ $hostname != 'localhost' ]] && return 0 || return 1
|
[[ $hostname =~ ^[a-zA-Z0-9\-]+$ ]] && [[ $hostname != 'localhost' ]] && return 0 || return 1
|
||||||
}
|
}
|
||||||
|
|
||||||
verify_ip4() {
|
|
||||||
local ip=$1
|
|
||||||
# Is this an IP or CIDR?
|
|
||||||
if grep -qP "^[^/]+/[^/]+$" <<< $ip; then
|
|
||||||
# Looks like a CIDR
|
|
||||||
valid_ip4_cidr_mask "$ip"
|
|
||||||
else
|
|
||||||
# We know this is not a CIDR - Is it an IP?
|
|
||||||
valid_ip4 "$ip"
|
|
||||||
fi
|
|
||||||
}
|
|
||||||
|
|
||||||
valid_ip4() {
|
valid_ip4() {
|
||||||
local ip=$1
|
local ip=$1
|
||||||
|
|
||||||
@@ -740,23 +601,6 @@ valid_username() {
|
|||||||
echo "$user" | grep -qP '^[a-z_]([a-z0-9_-]{0,31}|[a-z0-9_-]{0,30}\$)$' && return 0 || return 1
|
echo "$user" | grep -qP '^[a-z_]([a-z0-9_-]{0,31}|[a-z0-9_-]{0,30}\$)$' && return 0 || return 1
|
||||||
}
|
}
|
||||||
|
|
||||||
verify_md5_checksum() {
|
|
||||||
data_file=$1
|
|
||||||
md5_file=${2:-${data_file}.md5}
|
|
||||||
|
|
||||||
if [[ ! -f "$dest_file" || ! -f "$md5_file" ]]; then
|
|
||||||
return 2
|
|
||||||
fi
|
|
||||||
|
|
||||||
SOURCEHASH=$(md5sum "$data_file" | awk '{ print $1 }')
|
|
||||||
HASH=$(cat "$md5_file")
|
|
||||||
|
|
||||||
if [[ "$HASH" == "$SOURCEHASH" ]]; then
|
|
||||||
return 0
|
|
||||||
fi
|
|
||||||
return 1
|
|
||||||
}
|
|
||||||
|
|
||||||
wait_for_web_response() {
|
wait_for_web_response() {
|
||||||
url=$1
|
url=$1
|
||||||
expected=$2
|
expected=$2
|
||||||
|
|||||||
@@ -1,52 +0,0 @@
|
|||||||
#!/usr/bin/env python3
|
|
||||||
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
|
||||||
# Elastic License 2.0.
|
|
||||||
|
|
||||||
import sys
|
|
||||||
import subprocess
|
|
||||||
import os
|
|
||||||
|
|
||||||
sys.path.append('/opt/saltstack/salt/lib/python3.10/site-packages/')
|
|
||||||
import salt.config
|
|
||||||
import salt.loader
|
|
||||||
|
|
||||||
__opts__ = salt.config.minion_config('/etc/salt/minion')
|
|
||||||
__grains__ = salt.loader.grains(__opts__)
|
|
||||||
|
|
||||||
def check_needs_restarted():
|
|
||||||
osfam = __grains__['os_family']
|
|
||||||
val = '0'
|
|
||||||
outfile = "/opt/so/log/sostatus/needs_restarted"
|
|
||||||
|
|
||||||
if osfam == 'Debian':
|
|
||||||
if os.path.exists('/var/run/reboot-required'):
|
|
||||||
val = '1'
|
|
||||||
elif osfam == 'RedHat':
|
|
||||||
cmd = 'needs-restarting -r > /dev/null 2>&1'
|
|
||||||
try:
|
|
||||||
needs_restarting = subprocess.check_call(cmd, shell=True)
|
|
||||||
except subprocess.CalledProcessError:
|
|
||||||
val = '1'
|
|
||||||
else:
|
|
||||||
fail("Unsupported OS")
|
|
||||||
|
|
||||||
with open(outfile, 'w') as f:
|
|
||||||
f.write(val)
|
|
||||||
|
|
||||||
def fail(msg):
|
|
||||||
print(msg, file=sys.stderr)
|
|
||||||
sys.exit(1)
|
|
||||||
|
|
||||||
|
|
||||||
def main():
|
|
||||||
proc = subprocess.run(['id', '-u'], stdout=subprocess.PIPE, encoding="utf-8")
|
|
||||||
if proc.stdout.strip() != "0":
|
|
||||||
fail("This program must be run as root")
|
|
||||||
|
|
||||||
check_needs_restarted()
|
|
||||||
|
|
||||||
if __name__ == "__main__":
|
|
||||||
main()
|
|
||||||
48
salt/common/tools/sbin/so-config-backup
Executable file
@@ -0,0 +1,48 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.. /usr/sbin/so-common
|
||||||
|
{% set BACKUPLOCATIONS = salt['pillar.get']('backup:locations', {}) %}
|
||||||
|
|
||||||
|
TODAY=$(date '+%Y_%m_%d')
|
||||||
|
BACKUPFILE="/nsm/backup/so-config-backup-$TODAY.tar"
|
||||||
|
MAXBACKUPS=7
|
||||||
|
|
||||||
|
# Create backup dir if it does not exist
|
||||||
|
mkdir -p /nsm/backup
|
||||||
|
|
||||||
|
# If we haven't already written a backup file for today, let's do so
|
||||||
|
if [ ! -f $BACKUPFILE ]; then
|
||||||
|
|
||||||
|
# Create empty backup file
|
||||||
|
tar -cf $BACKUPFILE -T /dev/null
|
||||||
|
|
||||||
|
# Loop through all paths defined in global.sls, and append them to backup file
|
||||||
|
{%- for LOCATION in BACKUPLOCATIONS %}
|
||||||
|
tar -rf $BACKUPFILE {{ LOCATION }}
|
||||||
|
{%- endfor %}
|
||||||
|
tar -rf $BACKUPFILE /etc/pki
|
||||||
|
tar -rf $BACKUPFILE /etc/salt
|
||||||
|
tar -rf $BACKUPFILE /opt/so/conf/kratos
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
|
# Find oldest backup files and remove them
|
||||||
|
NUMBACKUPS=$(find /nsm/backup/ -type f -name "so-config-backup*" | wc -l)
|
||||||
|
while [ "$NUMBACKUPS" -gt "$MAXBACKUPS" ]; do
|
||||||
|
OLDESTBACKUP=$(find /nsm/backup/ -type f -name "so-config-backup*" -type f -printf '%T+ %p\n' | sort | head -n 1 | awk -F" " '{print $2}')
|
||||||
|
rm -f $OLDESTBACKUP
|
||||||
|
NUMBACKUPS=$(find /nsm/backup/ -type f -name "so-config-backup*" | wc -l)
|
||||||
|
done
|
||||||
20
salt/common/tools/sbin/so-cortex-restart
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
echo "TheHive and its components are no longer part of Security Onion"
|
||||||
20
salt/common/tools/sbin/so-cortex-start
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
echo "TheHive and its components are no longer part of Security Onion"
|
||||||
20
salt/common/tools/sbin/so-cortex-stop
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
echo "TheHive and its components are no longer part of Security Onion"
|
||||||
20
salt/common/tools/sbin/so-cortex-user-add
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
echo "TheHive and its components are no longer part of Security Onion"
|
||||||
20
salt/common/tools/sbin/so-cortex-user-enable
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
echo "TheHive and its components are no longer part of Security Onion"
|
||||||
20
salt/common/tools/sbin/so-curator-restart
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
/usr/sbin/so-restart curator $1
|
||||||
20
salt/common/tools/sbin/so-curator-start
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
/usr/sbin/so-start curator $1
|
||||||
20
salt/common/tools/sbin/so-curator-stop
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
/usr/sbin/so-stop curator $1
|
||||||
@@ -1,11 +1,19 @@
|
|||||||
#!/usr/bin/env python3
|
#!/usr/bin/env python3
|
||||||
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
#
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
# This program is free software: you can redistribute it and/or modify
|
||||||
# Elastic License 2.0.
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
import ipaddress
|
import ipaddress
|
||||||
import textwrap
|
import textwrap
|
||||||
@@ -19,12 +27,17 @@ from xml.dom import minidom
|
|||||||
|
|
||||||
|
|
||||||
LOCAL_SALT_DIR='/opt/so/saltstack/local'
|
LOCAL_SALT_DIR='/opt/so/saltstack/local'
|
||||||
|
WAZUH_CONF='/nsm/wazuh/etc/ossec.conf'
|
||||||
VALID_ROLES = {
|
VALID_ROLES = {
|
||||||
'a': { 'role': 'analyst','desc': 'Analyst - 80/tcp, 443/tcp' },
|
'a': { 'role': 'analyst','desc': 'Analyst - 80/tcp, 443/tcp' },
|
||||||
'b': { 'role': 'beats_endpoint', 'desc': 'Logstash Beat - 5044/tcp' },
|
'b': { 'role': 'beats_endpoint', 'desc': 'Logstash Beat - 5044/tcp' },
|
||||||
'e': { 'role': 'elasticsearch_rest', 'desc': 'Elasticsearch REST API - 9200/tcp' },
|
'e': { 'role': 'elasticsearch_rest', 'desc': 'Elasticsearch REST API - 9200/tcp' },
|
||||||
'f': { 'role': 'strelka_frontend', 'desc': 'Strelka frontend - 57314/tcp' },
|
'f': { 'role': 'strelka_frontend', 'desc': 'Strelka frontend - 57314/tcp' },
|
||||||
|
'o': { 'role': 'osquery_endpoint', 'desc': 'Osquery endpoint - 8090/tcp' },
|
||||||
's': { 'role': 'syslog', 'desc': 'Syslog device - 514/tcp/udp' },
|
's': { 'role': 'syslog', 'desc': 'Syslog device - 514/tcp/udp' },
|
||||||
|
'w': { 'role': 'wazuh_agent', 'desc': 'Wazuh agent - 1514/tcp/udp' },
|
||||||
|
'p': { 'role': 'wazuh_api', 'desc': 'Wazuh API - 55000/tcp' },
|
||||||
|
'r': { 'role': 'wazuh_authd', 'desc': 'Wazuh registration service - 1515/tcp' }
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
||||||
@@ -63,15 +76,73 @@ def ip_prompt() -> str:
|
|||||||
sys.exit(1)
|
sys.exit(1)
|
||||||
|
|
||||||
|
|
||||||
|
def wazuh_enabled() -> bool:
|
||||||
|
for file in os.listdir(f'{LOCAL_SALT_DIR}/pillar'):
|
||||||
|
with open(file, 'r') as pillar:
|
||||||
|
if 'wazuh: 1' in pillar.read():
|
||||||
|
return True
|
||||||
|
return False
|
||||||
|
|
||||||
|
|
||||||
|
def root_to_str(root: ET.ElementTree) -> str:
|
||||||
|
xml_str = ET.tostring(root, encoding='unicode', method='xml').replace('\n', '')
|
||||||
|
xml_str = re.sub(r'(?:(?<=>) *)', '', xml_str)
|
||||||
|
|
||||||
|
# Remove specific substrings to better format comments on intial parse/write
|
||||||
|
xml_str = re.sub(r' -', '', xml_str)
|
||||||
|
xml_str = re.sub(r' -->', ' -->', xml_str)
|
||||||
|
|
||||||
|
dom = minidom.parseString(xml_str)
|
||||||
|
return dom.toprettyxml(indent=" ")
|
||||||
|
|
||||||
|
|
||||||
|
def rem_wl(ip):
|
||||||
|
parser = ET.XMLParser(remove_blank_text=True)
|
||||||
|
with open(WAZUH_CONF, 'rb') as wazuh_conf:
|
||||||
|
tree = ET.parse(wazuh_conf, parser)
|
||||||
|
root = tree.getroot()
|
||||||
|
|
||||||
|
global_elems = root.findall(f"global/white_list[. = '{ip}']/..")
|
||||||
|
if len(global_elems) > 0:
|
||||||
|
for g_elem in global_elems:
|
||||||
|
ge_index = list(root).index(g_elem)
|
||||||
|
if ge_index > 0 and root[list(root).index(g_elem) - 1].tag == ET.Comment:
|
||||||
|
root.remove(root[ge_index - 1])
|
||||||
|
root.remove(g_elem)
|
||||||
|
|
||||||
|
with open(WAZUH_CONF, 'w') as out:
|
||||||
|
out.write(root_to_str(root))
|
||||||
|
|
||||||
|
|
||||||
def apply(role: str, ip: str) -> int:
|
def apply(role: str, ip: str) -> int:
|
||||||
firewall_cmd = ['so-firewall', 'excludehost', role, ip]
|
firewall_cmd = ['so-firewall', 'excludehost', role, ip]
|
||||||
salt_cmd = ['salt-call', 'state.apply', '-l', 'quiet', 'firewall', 'queue=True']
|
salt_cmd = ['salt-call', 'state.apply', '-l', 'quiet', 'firewall', 'queue=True']
|
||||||
|
restart_wazuh_cmd = ['so-wazuh-restart']
|
||||||
print(f'Removing {ip} from the {role} role. This can take a few seconds...')
|
print(f'Removing {ip} from the {role} role. This can take a few seconds...')
|
||||||
cmd = subprocess.run(firewall_cmd)
|
cmd = subprocess.run(firewall_cmd)
|
||||||
if cmd.returncode == 0:
|
if cmd.returncode == 0:
|
||||||
cmd = subprocess.run(salt_cmd, stdout=subprocess.DEVNULL)
|
cmd = subprocess.run(salt_cmd, stdout=subprocess.DEVNULL)
|
||||||
else:
|
else:
|
||||||
return cmd.returncode
|
return cmd.returncode
|
||||||
|
if cmd.returncode == 0:
|
||||||
|
if wazuh_enabled and role=='analyst':
|
||||||
|
try:
|
||||||
|
rem_wl(ip)
|
||||||
|
print(f'Removed whitelist entry for {ip} from {WAZUH_CONF}', file=sys.stderr)
|
||||||
|
except Exception as e:
|
||||||
|
print(f'Failed to remove whitelist entry for {ip} from {WAZUH_CONF}', file=sys.stderr)
|
||||||
|
print(e)
|
||||||
|
return 1
|
||||||
|
print('Restarting OSSEC Server...')
|
||||||
|
cmd = subprocess.run(restart_wazuh_cmd)
|
||||||
|
else:
|
||||||
|
return cmd.returncode
|
||||||
|
else:
|
||||||
|
print(f'Commmand \'{" ".join(salt_cmd)}\' failed.', file=sys.stderr)
|
||||||
|
return cmd.returncode
|
||||||
|
if cmd.returncode != 0:
|
||||||
|
print('Failed to restart OSSEC server.')
|
||||||
|
return cmd.returncode
|
||||||
|
|
||||||
|
|
||||||
def main():
|
def main():
|
||||||
@@ -92,7 +163,11 @@ def main():
|
|||||||
group.add_argument('-b', dest='roles', action='append_const', const=VALID_ROLES['b']['role'], help="Logstash Beat - 5044/tcp")
|
group.add_argument('-b', dest='roles', action='append_const', const=VALID_ROLES['b']['role'], help="Logstash Beat - 5044/tcp")
|
||||||
group.add_argument('-e', dest='roles', action='append_const', const=VALID_ROLES['e']['role'], help="Elasticsearch REST API - 9200/tcp")
|
group.add_argument('-e', dest='roles', action='append_const', const=VALID_ROLES['e']['role'], help="Elasticsearch REST API - 9200/tcp")
|
||||||
group.add_argument('-f', dest='roles', action='append_const', const=VALID_ROLES['f']['role'], help="Strelka frontend - 57314/tcp")
|
group.add_argument('-f', dest='roles', action='append_const', const=VALID_ROLES['f']['role'], help="Strelka frontend - 57314/tcp")
|
||||||
|
group.add_argument('-o', dest='roles', action='append_const', const=VALID_ROLES['o']['role'], help="Osquery endpoint - 8090/tcp")
|
||||||
group.add_argument('-s', dest='roles', action='append_const', const=VALID_ROLES['s']['role'], help="Syslog device - 514/tcp/udp")
|
group.add_argument('-s', dest='roles', action='append_const', const=VALID_ROLES['s']['role'], help="Syslog device - 514/tcp/udp")
|
||||||
|
group.add_argument('-w', dest='roles', action='append_const', const=VALID_ROLES['w']['role'], help="Wazuh agent - 1514/tcp/udp")
|
||||||
|
group.add_argument('-p', dest='roles', action='append_const', const=VALID_ROLES['p']['role'], help="Wazuh API - 55000/tcp")
|
||||||
|
group.add_argument('-r', dest='roles', action='append_const', const=VALID_ROLES['r']['role'], help="Wazuh registration service - 1515/tcp")
|
||||||
|
|
||||||
ip_g = main_parser.add_argument_group(title='allow')
|
ip_g = main_parser.add_argument_group(title='allow')
|
||||||
ip_g.add_argument('-i', help="IP or CIDR block to disallow connections from, requires at least one role argument", metavar='', dest='ip')
|
ip_g.add_argument('-i', help="IP or CIDR block to disallow connections from, requires at least one role argument", metavar='', dest='ip')
|
||||||
@@ -1,11 +1,19 @@
|
|||||||
#!/usr/bin/env python3
|
#!/usr/bin/env python3
|
||||||
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
#
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
# This program is free software: you can redistribute it and/or modify
|
||||||
# Elastic License 2.0.
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
import sys, argparse, re, docker
|
import sys, argparse, re, docker
|
||||||
from packaging.version import Version, InvalidVersion
|
from packaging.version import Version, InvalidVersion
|
||||||
|
|||||||
22
salt/common/tools/sbin/so-docker-refresh
Executable file
@@ -0,0 +1,22 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
. /usr/sbin/so-image-common
|
||||||
|
|
||||||
|
require_manager
|
||||||
|
update_docker_containers "refresh"
|
||||||
20
salt/common/tools/sbin/so-elastalert-restart
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
/usr/sbin/so-restart elastalert $1
|
||||||
20
salt/common/tools/sbin/so-elastalert-start
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
/usr/sbin/so-start elastalert $1
|
||||||
20
salt/common/tools/sbin/so-elastalert-stop
Executable file
@@ -0,0 +1,20 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
/usr/sbin/so-stop elastalert $1
|
||||||
67
salt/common/tools/sbin/so-elastic-auth
Executable file
@@ -0,0 +1,67 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
if [ -f "/usr/sbin/so-common" ]; then
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
fi
|
||||||
|
|
||||||
|
ES_AUTH_PILLAR=${ELASTIC_AUTH_PILLAR:-/opt/so/saltstack/local/pillar/elasticsearch/auth.sls}
|
||||||
|
ES_USERS_FILE=${ELASTIC_USERS_FILE:-/opt/so/saltstack/local/salt/elasticsearch/files/users}
|
||||||
|
|
||||||
|
authEnable=$1
|
||||||
|
|
||||||
|
if ! grep -q "enabled: " "$ES_AUTH_PILLAR"; then
|
||||||
|
echo "Elastic auth pillar file is invalid. Unable to proceed."
|
||||||
|
exit 1
|
||||||
|
fi
|
||||||
|
|
||||||
|
function restart() {
|
||||||
|
if [[ -z "$ELASTIC_AUTH_SKIP_HIGHSTATE" ]]; then
|
||||||
|
echo "Elasticsearch on all affected minions will now be stopped and then restarted..."
|
||||||
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode' cmd.run so-elastic-stop queue=True
|
||||||
|
echo "Applying highstate to all affected minions..."
|
||||||
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode' state.highstate queue=True
|
||||||
|
fi
|
||||||
|
}
|
||||||
|
|
||||||
|
if [[ "$authEnable" == "true" ]]; then
|
||||||
|
if grep -q "enabled: False" "$ES_AUTH_PILLAR"; then
|
||||||
|
sed -i 's/enabled: False/enabled: True/g' "$ES_AUTH_PILLAR"
|
||||||
|
restart
|
||||||
|
echo "Elastic auth is now enabled."
|
||||||
|
if grep -q "argon" "$ES_USERS_FILE"; then
|
||||||
|
echo ""
|
||||||
|
echo "IMPORTANT: The following users will need to change their password, after logging into SOC, in order to access Kibana:"
|
||||||
|
grep argon "$ES_USERS_FILE" | cut -d ":" -f 1
|
||||||
|
fi
|
||||||
|
else
|
||||||
|
echo "Auth is already enabled."
|
||||||
|
fi
|
||||||
|
elif [[ "$authEnable" == "false" ]]; then
|
||||||
|
if grep -q "enabled: True" "$ES_AUTH_PILLAR"; then
|
||||||
|
sed -i 's/enabled: True/enabled: False/g' "$ES_AUTH_PILLAR"
|
||||||
|
restart
|
||||||
|
echo "Elastic auth is now disabled."
|
||||||
|
else
|
||||||
|
echo "Auth is already disabled."
|
||||||
|
fi
|
||||||
|
else
|
||||||
|
echo "Usage: $0 <true|false>"
|
||||||
|
echo ""
|
||||||
|
echo "Toggles Elastic authentication. Elasticsearch will be restarted on each affected minion."
|
||||||
|
echo ""
|
||||||
|
fi
|
||||||
27
salt/manager/tools/sbin/so-elastic-auth-password-reset → salt/common/tools/sbin/so-elastic-auth-password-reset
Executable file → Normal file
@@ -1,10 +1,19 @@
|
|||||||
#!/bin/bash
|
#!/bin/bash
|
||||||
|
|
||||||
# Copyright Security Onion Solutions LLC and/or licensed to Security Onion Solutions LLC under one
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
# or more contributor license agreements. Licensed under the Elastic License 2.0 as shown at
|
|
||||||
# https://securityonion.net/license; you may not use this file except in compliance with the
|
|
||||||
# Elastic License 2.0.
|
|
||||||
|
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
source $(dirname $0)/so-common
|
source $(dirname $0)/so-common
|
||||||
require_manager
|
require_manager
|
||||||
@@ -89,14 +98,18 @@ function killAllSaltJobs() {
|
|||||||
function soUserSync() {
|
function soUserSync() {
|
||||||
# apply this state to update /opt/so/saltstack/local/salt/elasticsearch/curl.config on the manager
|
# apply this state to update /opt/so/saltstack/local/salt/elasticsearch/curl.config on the manager
|
||||||
salt-call state.sls_id elastic_curl_config_distributed manager queue=True
|
salt-call state.sls_id elastic_curl_config_distributed manager queue=True
|
||||||
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-searchnode or G@role:so-heavynode' saltutil.kill_all_jobs
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode' saltutil.kill_all_jobs
|
||||||
# apply this state to get the curl.config
|
# apply this state to get the curl.config
|
||||||
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-searchnode or G@role:so-heavynode' state.sls_id elastic_curl_config common queue=True
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode' state.sls_id elastic_curl_config common queue=True
|
||||||
$(dirname $0)/so-user sync
|
$(dirname $0)/so-user sync
|
||||||
printf "\nApplying logstash state to the appropriate nodes.\n\n"
|
printf "\nApplying logstash state to the appropriate nodes.\n\n"
|
||||||
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-searchnode or G@role:so-heavynode' state.apply logstash queue=True
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode' state.apply logstash queue=True
|
||||||
|
printf "\nApplying filebeat state to the appropriate nodes.\n\n"
|
||||||
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode or G@role:so-sensor or G@role:so-fleet' state.apply filebeat queue=True
|
||||||
printf "\nApplying kibana state to the appropriate nodes.\n\n"
|
printf "\nApplying kibana state to the appropriate nodes.\n\n"
|
||||||
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch' state.apply kibana queue=True
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch' state.apply kibana queue=True
|
||||||
|
printf "\nApplying curator state to the appropriate nodes.\n\n"
|
||||||
|
salt -C 'G@role:so-standalone or G@role:so-eval or G@role:so-import or G@role:so-manager or G@role:so-managersearch or G@role:so-node or G@role:so-heavynode' state.apply curator queue=True
|
||||||
}
|
}
|
||||||
|
|
||||||
function highstateManager() {
|
function highstateManager() {
|
||||||
116
salt/common/tools/sbin/so-elastic-clear
Executable file
@@ -0,0 +1,116 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
SKIP=0
|
||||||
|
#########################################
|
||||||
|
# Options
|
||||||
|
#########################################
|
||||||
|
usage()
|
||||||
|
{
|
||||||
|
cat <<EOF
|
||||||
|
Security Onion Elastic Clear
|
||||||
|
Options:
|
||||||
|
-h This message
|
||||||
|
-y Skip interactive mode
|
||||||
|
EOF
|
||||||
|
}
|
||||||
|
while getopts "h:y" OPTION
|
||||||
|
do
|
||||||
|
case $OPTION in
|
||||||
|
h)
|
||||||
|
usage
|
||||||
|
exit 0
|
||||||
|
;;
|
||||||
|
|
||||||
|
y)
|
||||||
|
SKIP=1
|
||||||
|
;;
|
||||||
|
*)
|
||||||
|
usage
|
||||||
|
exit 0
|
||||||
|
;;
|
||||||
|
esac
|
||||||
|
done
|
||||||
|
if [ $SKIP -ne 1 ]; then
|
||||||
|
# List indices
|
||||||
|
echo
|
||||||
|
{{ ELASTICCURL }} -k -L https://{{ NODEIP }}:9200/_cat/indices?v
|
||||||
|
echo
|
||||||
|
# Inform user we are about to delete all data
|
||||||
|
echo
|
||||||
|
echo "This script will delete all data (documents, indices, etc.) in the Elasticsearch database."
|
||||||
|
echo
|
||||||
|
echo "If you would like to proceed, please type "AGREE" and hit ENTER."
|
||||||
|
echo
|
||||||
|
# Read user input
|
||||||
|
read INPUT
|
||||||
|
if [ "$INPUT" != "AGREE" ] ; then exit 0; fi
|
||||||
|
fi
|
||||||
|
|
||||||
|
# Check to see if Logstash/Filebeat are running
|
||||||
|
LS_ENABLED=$(so-status | grep logstash)
|
||||||
|
FB_ENABLED=$(so-status | grep filebeat)
|
||||||
|
EA_ENABLED=$(so-status | grep elastalert)
|
||||||
|
|
||||||
|
if [ ! -z "$FB_ENABLED" ]; then
|
||||||
|
|
||||||
|
/usr/sbin/so-filebeat-stop
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ ! -z "$LS_ENABLED" ]; then
|
||||||
|
|
||||||
|
/usr/sbin/so-logstash-stop
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ ! -z "$EA_ENABLED" ]; then
|
||||||
|
|
||||||
|
/usr/sbin/so-elastalert-stop
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
|
# Delete data
|
||||||
|
echo "Deleting data..."
|
||||||
|
|
||||||
|
INDXS=$({{ ELASTICCURL }} -s -XGET -k -L https://{{ NODEIP }}:9200/_cat/indices?v | egrep 'logstash|elastalert|so-' | awk '{ print $3 }')
|
||||||
|
for INDX in ${INDXS}
|
||||||
|
do
|
||||||
|
{{ ELASTICCURL }} -XDELETE -k -L https://"{{ NODEIP }}:9200/${INDX}" > /dev/null 2>&1
|
||||||
|
done
|
||||||
|
|
||||||
|
#Start Logstash/Filebeat
|
||||||
|
if [ ! -z "$FB_ENABLED" ]; then
|
||||||
|
|
||||||
|
/usr/sbin/so-filebeat-start
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ ! -z "$LS_ENABLED" ]; then
|
||||||
|
|
||||||
|
/usr/sbin/so-logstash-start
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ ! -z "$EA_ENABLED" ]; then
|
||||||
|
|
||||||
|
/usr/sbin/so-elastalert-start
|
||||||
|
|
||||||
|
fi
|
||||||
|
|
||||||
33
salt/common/tools/sbin/so-elastic-diagnose
Executable file
@@ -0,0 +1,33 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
# Source common settings
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
# Check for log files
|
||||||
|
for FILE in /opt/so/log/elasticsearch/*.log /opt/so/log/logstash/*.log /opt/so/log/kibana/*.log /opt/so/log/elastalert/*.log /opt/so/log/curator/*.log /opt/so/log/freqserver/*.log /opt/so/log/nginx/*.log; do
|
||||||
|
|
||||||
|
# If file exists, then look for errors or warnings
|
||||||
|
if [ -f $FILE ]; then
|
||||||
|
MESSAGE=`grep -i 'ERROR\|FAIL\|WARN' $FILE`
|
||||||
|
if [ ! -z "$MESSAGE" ]; then
|
||||||
|
header $FILE
|
||||||
|
echo $MESSAGE | sed 's/WARN/\nWARN/g' | sed 's/WARNING/\nWARNING/g' | sed 's/ERROR/\nERROR/g' | sort | uniq -c | sort -nr
|
||||||
|
echo
|
||||||
|
fi
|
||||||
|
fi
|
||||||
|
done
|
||||||
43
salt/common/tools/sbin/so-elastic-restart
Executable file
@@ -0,0 +1,43 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval','so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node', 'so-import']%}
|
||||||
|
/usr/sbin/so-restart elasticsearch $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval', 'so-manager', 'so-managersearch', 'so-standalone', 'so-import']%}
|
||||||
|
/usr/sbin/so-restart kibana $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node']%}
|
||||||
|
/usr/sbin/so-restart logstash $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node', 'so-sensor']%}
|
||||||
|
/usr/sbin/so-restart filebeat $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node']%}
|
||||||
|
/usr/sbin/so-restart curator $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval','so-manager', 'so-managersearch', 'so-standalone']%}
|
||||||
|
/usr/sbin/so-restart elastalert $1
|
||||||
|
{%- endif %}
|
||||||
43
salt/common/tools/sbin/so-elastic-start
Executable file
@@ -0,0 +1,43 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval','so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node', 'so-import']%}
|
||||||
|
/usr/sbin/so-start elasticsearch $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval', 'so-manager', 'so-managersearch', 'so-standalone', 'so-import']%}
|
||||||
|
/usr/sbin/so-start kibana $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node']%}
|
||||||
|
/usr/sbin/so-start logstash $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node', 'so-sensor']%}
|
||||||
|
/usr/sbin/so-start filebeat $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node']%}
|
||||||
|
/usr/sbin/so-start curator $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval','so-manager', 'so-managersearch', 'so-standalone']%}
|
||||||
|
/usr/sbin/so-start elastalert $1
|
||||||
|
{%- endif %}
|
||||||
43
salt/common/tools/sbin/so-elastic-stop
Executable file
@@ -0,0 +1,43 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval','so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node', 'so-import']%}
|
||||||
|
/usr/sbin/so-stop elasticsearch $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval', 'so-manager', 'so-managersearch', 'so-standalone', 'so-import']%}
|
||||||
|
/usr/sbin/so-stop kibana $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node']%}
|
||||||
|
/usr/sbin/so-stop logstash $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node', 'so-sensor']%}
|
||||||
|
/usr/sbin/so-stop filebeat $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-manager', 'so-managersearch', 'so-standalone', 'so-heavynode', 'so-node']%}
|
||||||
|
/usr/sbin/so-stop curator $1
|
||||||
|
{%- endif %}
|
||||||
|
|
||||||
|
{%- if grains['role'] in ['so-eval','so-manager', 'so-managersearch', 'so-standalone']%}
|
||||||
|
/usr/sbin/so-stop elastalert $1
|
||||||
|
{%- endif %}
|
||||||
23
salt/common/tools/sbin/so-elasticsearch-component-templates-list
Executable file
@@ -0,0 +1,23 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
if [ "$1" == "" ]; then
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_component_template | jq '.component_templates[] |.name'| sort
|
||||||
|
else
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_component_template/$1 | jq
|
||||||
|
fi
|
||||||
23
salt/common/tools/sbin/so-elasticsearch-index-templates-list
Executable file
@@ -0,0 +1,23 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
if [ "$1" == "" ]; then
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_index_template | jq '.index_templates[] |.name'| sort
|
||||||
|
else
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_index_template/$1 | jq
|
||||||
|
fi
|
||||||
21
salt/common/tools/sbin/so-elasticsearch-indices-list
Executable file
@@ -0,0 +1,21 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
{{ ELASTICCURL }} -s -k -L "https://{{ NODEIP }}:9200/_cat/indices?pretty&v&s=index"
|
||||||
23
salt/common/tools/sbin/so-elasticsearch-indices-rw
Executable file
@@ -0,0 +1,23 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
IP={{ salt['grains.get']('ip_interfaces').get(salt['pillar.get']('sensor:mainint', salt['pillar.get']('manager:mainint', salt['pillar.get']('elasticsearch:mainint', salt['pillar.get']('host:mainint')))))[0] }}
|
||||||
|
ESPORT=9200
|
||||||
|
|
||||||
|
echo "Removing read only attributes for indices..."
|
||||||
|
echo
|
||||||
|
{{ ELASTICCURL }} -s -k -XPUT -H "Content-Type: application/json" -L https://$IP:9200/_all/_settings -d '{"index.blocks.read_only_allow_delete": null}' 2>&1 | if grep -q ack; then echo "Index settings updated..."; else echo "There was any issue updating the read-only attribute. Please ensure Elasticsearch is running.";fi;
|
||||||
25
salt/common/tools/sbin/so-elasticsearch-pipeline-stats
Executable file
@@ -0,0 +1,25 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
if [ "$1" == "" ]; then
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_nodes/stats | jq .nodes | jq ".[] | .ingest.pipelines"
|
||||||
|
else
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_nodes/stats | jq .nodes | jq ".[] | .ingest.pipelines.\"$1\""
|
||||||
|
fi
|
||||||
25
salt/common/tools/sbin/so-elasticsearch-pipeline-view
Executable file
@@ -0,0 +1,25 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
|
||||||
|
if [ "$1" == "" ]; then
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_ingest/pipeline/* | jq .
|
||||||
|
else
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_ingest/pipeline/$1 | jq .[]
|
||||||
|
fi
|
||||||
23
salt/common/tools/sbin/so-elasticsearch-pipelines-list
Executable file
@@ -0,0 +1,23 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# Copyright 2014-2022 Security Onion Solutions, LLC
|
||||||
|
#
|
||||||
|
# This program is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU General Public License as published by
|
||||||
|
# the Free Software Foundation, either version 3 of the License, or
|
||||||
|
# (at your option) any later version.
|
||||||
|
#
|
||||||
|
# This program is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU General Public License
|
||||||
|
# along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||||
|
{%- set NODEIP = salt['pillar.get']('elasticsearch:mainip', '') -%}
|
||||||
|
. /usr/sbin/so-common
|
||||||
|
if [ "$1" == "" ]; then
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_ingest/pipeline/* | jq 'keys'
|
||||||
|
else
|
||||||
|
{{ ELASTICCURL }} -s -k -L https://{{ NODEIP }}:9200/_ingest/pipeline/$1 | jq
|
||||||
|
fi
|
||||||